Jan 28, 2026
Global KYC and AML Regulations: Part 2 - From Compliance to Confidence
Global KYC and AML Regulations: Part 2 - From Compliance to Confidence
Global KYC and AML Regulations: Part 2 - From Compliance to Confidence
Fraud moves across channels, teams, and moments in the customer journey. To keep pace, businesses need more than separate KYC, AML, and fraud checks. By unifying risk signals earlier, businesses can prevent losses, protect customers, and make decisions with confidence.
Author
Team Bureau




TABLE OF CONTENTS
See Less
The post “Global KYC and AML Regulations: Part 1 - What Regulators Really Expect” of this 2-part blog series, explored how global regulators are shifting from procedural compliance to outcome-driven supervision. It explained how and why traditional KYC and AML approaches increasingly fall short.
Part 2 below, focuses on execution. It attempts to translate regulatory direction into practical best practices. It also discusses how leading institutions are aligning KYC, AML, fraud risk management (FRM), and device intelligence to execute proactive controls.
Fraud, account takeover, mule activity, and identity abuse follow almost similar patterns around the world. What changes is the speed at which those patterns emerge and the regulatory context within which businesses operate.
Regulatory language varies by geography. Risk does not.
Fraud adapts faster than regulation. It exploits gaps between onboarding and monitoring, between channels, and even between teams. Therefore, for institutions that treat KYC, AML, and fraud as separate functions, the chances of finding gaps is an uphill task.
Regional regulatory expectations and risk priorities
Regional regulatory expectations and risk priorities differ across major regions. These include:
India
India has context-aware risk-based controls. The regularity emphasis is on three major points:
Risk-based authentication
Transaction-level scrutiny
Reduced friction for low-risk users
Also, Indian regulators increasingly expect businesses to differentiate between low-risk and high-risk activity in real time, instead of relying on uniform controls.
Related Read: Risk-Based Authentication: How Can It Help Your Business?
There are several factors that have led to this regulatory stance. In India, the population exhibits several common traits such as:
SIM recycling and rapid number churn
Device sharing across individuals
Layered mule activity spanning accounts and apps
This makes static KYC insufficient to capture fraud complexity. Without device intelligence and behavioral context, businesses struggle to distinguish legitimate reuse from coordinated abuse. Identity assurance must, therefore, extend beyond documents to ongoing context.
Southeast Asia
One of the key traits of Southeast Asia is its rapid fintech adoption. However, it also suffers from inconsistent identity standards across countries. As a result it has high exposure to organized mule networks.
The current regulatory direction focuses on building stronger onboarding controls and putting in place stringent post-onboarding monitoring.
Related Read: What is a money mule?
In SEA markets, regulators increasingly recognize that identity verification at entry is necessary, but also insufficient. Risk commonly occurs way past the onboarding stage, as accounts are repurposed or recruited into fraud networks.
Financial institutions that want to win must focus on risk continuity: connecting identity signals across sessions, devices, and behaviors as users move quickly across platforms.

Middle East
The Middle East attracts a huge population of immigrants seeking employment opportunities in its developing real estate and energy sector. As a result, most of its risk exposure revolves around:
Cross-border payments and remittances
New digital rails and real-time settlement
Expanding attack surface tied to rapid digitization
Also, the Middle East has a progressive stance towards adopting AML frameworks.
As financial infrastructure modernizes, regulators expect risk controls to improve with it. Businesses are under pressure to demonstrate that faster payments and broader access do not come at the cost of increased financial crime exposure.
European Union
In the EU, effectiveness alone is not enough. Businesses must show how decisions are made, why certain signals were used, and how customer rights are respected throughout the process.
The regulatory environment has strong data protection requirements and zero tolerance for opaque or non-explainable decisions. Violations of GDPR can attract hefty penalties, such as in 2023, when approximately €2.1 billion in fines were imposed.
Region | Regulatory Focus | Primary Risk Drivers | Supervisory Expectations | Control Implications |
India | Context-aware, risk-tiered controls | Device reuse, SIM churn, mule layering | Real-time risk differentiation; adaptive controls | Continuous authentication, behavioral and device intelligence |
Southeast Asia | Identity continuity at scale | Fragmented ID systems, organized mule networks | Strong onboarding plus persistent monitoring | Cross-session identity linking and post-onboarding surveillance |
Middle East | Secure modernization of financial rails | Cross-border flows, rapid digitization | Crime controls that scale with payment speed and access | Real-time transaction monitoring and cross-border risk visibility |
European Union | Privacy, explainability, and accountability | Data misuse, opaque automation | Transparent, auditable decision-making | Explainable models, strict data governance, rights-preserving controls |
Best practices for KYC, AML, and FRM to adopt in 2026-27
Across regions, regulators are converging on the common principle that risk controls must be adaptive, continuous, and accountable.
How can businesses embrace these values for better KYC, AML, and FRM? These best practices show the way:
Move from document checks to identity assurance
Checklists confirm the existence of controls. Unfortunately, they do not confirm control.
Modern identity assurance treats trust as an ongoing state, not a one-time event. It continuously evaluates whether the same legitimate user remains in control of the account across sessions, devices, and behaviors.
This shift is critical for detecting account takeover, mule reuse, and synthetic identity abuse that documents alone cannot reveal.
Treat device intelligence as a first-class signal
Device intelligence is particularly necessary in environments where credentials are easily compromised or shared.
Devices carry more truth than credentials. They reveal certain traits that can be used to reveal underlying fraud patterns.
Often, without realizing, most users reveal:
Stability over time
Ownership patterns
Signs of manipulation or spoofing
Tracking and observing these signals are critical to identifying fraud signals before they snowball into full-sized catastrophes.

Use behavior to detect intent early
Fraud intent starts appearing way before fraud transactions happen. There are specific behavioral signals that, combined together, can help anticipate risk. These include:
Navigation patterns
Interaction timing
Environmental anomalies
These signals operate independently of transaction monitoring and provide an early-warning layer that traditional AML systems miss.
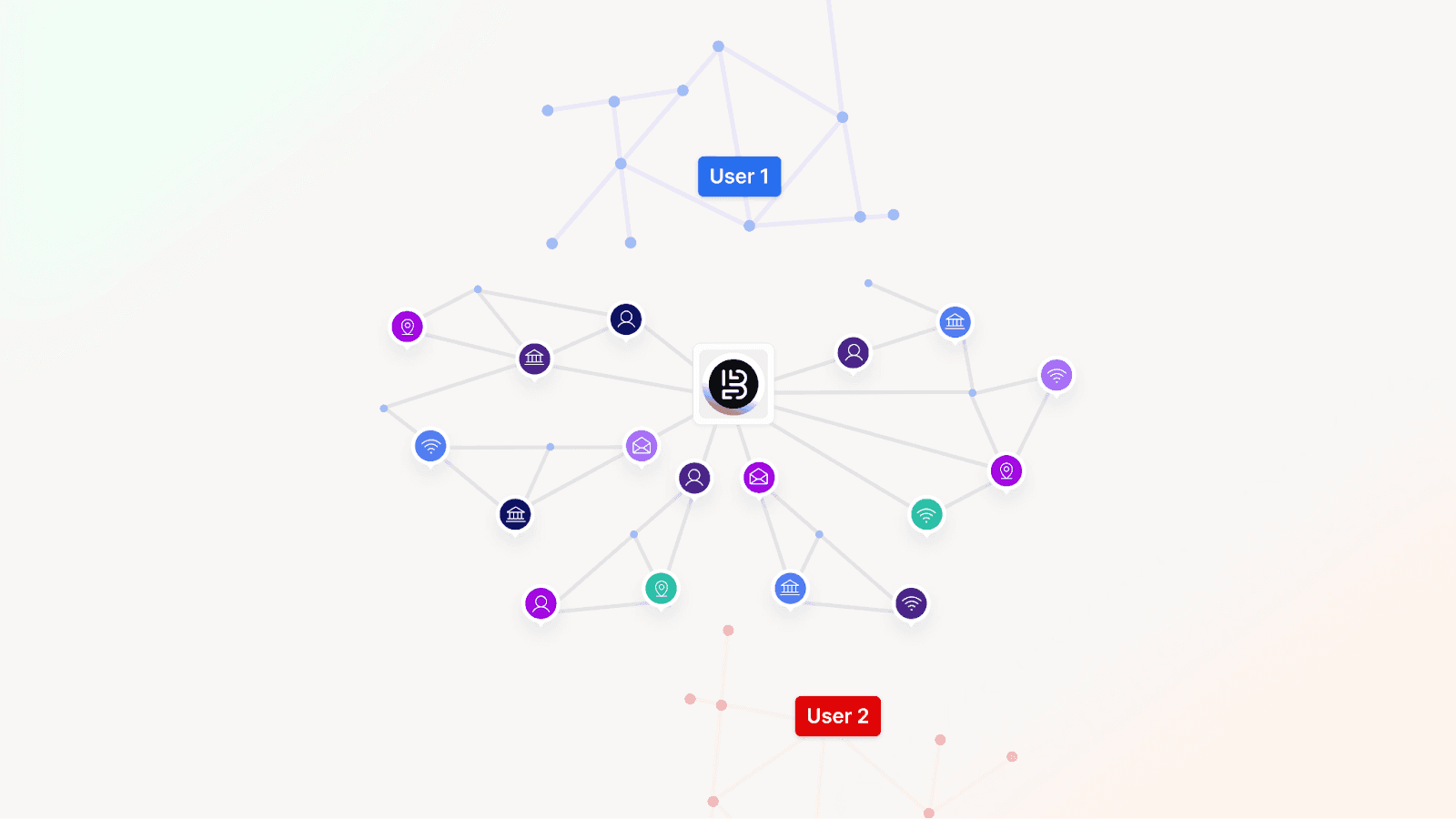
Connect identity across sessions and channels
Fraud rarely happens in isolation. It is usually orchestrated as part of a bigger plan, a sequence of events, and interdependent factors.
Attackers reuse devices, rotate credentials, and distribute activity across accounts and channels. Businesses that evaluate risk one session or one transaction at a time, miss the bigger picture.
Network-level intelligence which connects identities across time and touchpoints is far more effective than evaluating individuals in silos.
Reduce reliance on static rules
Static thresholds create blind spots, especially as attackers learn to operate just below them. Over time, rules accumulate, alerts increase, and effectiveness declines.
Modern risk programs rely on adaptive signals and decisioning frameworks that evolve with behavior, rather than chasing it.
Build explainable, auditable risk decisions
When fraud is discovered, knowing the cause and effect is insufficient. Businesses must dig deeper to understand the reason behind the fraud.
Unearthing the “why” behind the fraud will prove helpful in:
Regulatory audits
Internal governance
Cross-team trust
Clear decision flow such as the signals used, logic applied, outcome reached, and so forth, turns advanced risk intelligence into something regulators and executives can actually stand behind.
Related Read: Why the Future of Financial Crime Prevention Is Collaborative
Shift teams from alert handling to risk prevention
Smart security teams reduce operational burden by preventing risk earlier, rather than reacting to it later. This allows them to focus on control design, risk analysis, and continuous improvement, instead of manual firefighting.
The way forward: From compliance to confidence
KYC and AML remain essential foundations of trust and compliance. However, fraud risk management is the true differentiator.

Businesses that unify identity, device, behavior, and transaction intelligence move beyond just compliance to active risk prevention. They operate with the assurance that controls are effective, decisions are defensible, and customers are protected without unnecessary friction.
Modern risk management isn’t about more checks. It’s about making better decisions earlier, and with confidence.
Where Bureau fits in this FRM evolution
Bureau is built for businesses navigating the shift from procedural compliance to continuous, outcome-driven risk management. It acts as a unifying risk intelligence layer that connects identity, device, behavior, and transaction signals across the customer lifecycle.
By enabling context-aware decisioning, network-level visibility, and explainable risk outcomes, Bureau helps teams operationalize modern KYC, AML, and FRM principles without adding friction or complexity.
Move Beyond Compliance. Operate with Confidence.Discover how modern KYC, AML, and fraud risk teams are building adaptive, explainable, and continuous risk controls with Bureau. |
The post “Global KYC and AML Regulations: Part 1 - What Regulators Really Expect” of this 2-part blog series, explored how global regulators are shifting from procedural compliance to outcome-driven supervision. It explained how and why traditional KYC and AML approaches increasingly fall short.
Part 2 below, focuses on execution. It attempts to translate regulatory direction into practical best practices. It also discusses how leading institutions are aligning KYC, AML, fraud risk management (FRM), and device intelligence to execute proactive controls.
Fraud, account takeover, mule activity, and identity abuse follow almost similar patterns around the world. What changes is the speed at which those patterns emerge and the regulatory context within which businesses operate.
Regulatory language varies by geography. Risk does not.
Fraud adapts faster than regulation. It exploits gaps between onboarding and monitoring, between channels, and even between teams. Therefore, for institutions that treat KYC, AML, and fraud as separate functions, the chances of finding gaps is an uphill task.
Regional regulatory expectations and risk priorities
Regional regulatory expectations and risk priorities differ across major regions. These include:
India
India has context-aware risk-based controls. The regularity emphasis is on three major points:
Risk-based authentication
Transaction-level scrutiny
Reduced friction for low-risk users
Also, Indian regulators increasingly expect businesses to differentiate between low-risk and high-risk activity in real time, instead of relying on uniform controls.
Related Read: Risk-Based Authentication: How Can It Help Your Business?
There are several factors that have led to this regulatory stance. In India, the population exhibits several common traits such as:
SIM recycling and rapid number churn
Device sharing across individuals
Layered mule activity spanning accounts and apps
This makes static KYC insufficient to capture fraud complexity. Without device intelligence and behavioral context, businesses struggle to distinguish legitimate reuse from coordinated abuse. Identity assurance must, therefore, extend beyond documents to ongoing context.
Southeast Asia
One of the key traits of Southeast Asia is its rapid fintech adoption. However, it also suffers from inconsistent identity standards across countries. As a result it has high exposure to organized mule networks.
The current regulatory direction focuses on building stronger onboarding controls and putting in place stringent post-onboarding monitoring.
Related Read: What is a money mule?
In SEA markets, regulators increasingly recognize that identity verification at entry is necessary, but also insufficient. Risk commonly occurs way past the onboarding stage, as accounts are repurposed or recruited into fraud networks.
Financial institutions that want to win must focus on risk continuity: connecting identity signals across sessions, devices, and behaviors as users move quickly across platforms.

Middle East
The Middle East attracts a huge population of immigrants seeking employment opportunities in its developing real estate and energy sector. As a result, most of its risk exposure revolves around:
Cross-border payments and remittances
New digital rails and real-time settlement
Expanding attack surface tied to rapid digitization
Also, the Middle East has a progressive stance towards adopting AML frameworks.
As financial infrastructure modernizes, regulators expect risk controls to improve with it. Businesses are under pressure to demonstrate that faster payments and broader access do not come at the cost of increased financial crime exposure.
European Union
In the EU, effectiveness alone is not enough. Businesses must show how decisions are made, why certain signals were used, and how customer rights are respected throughout the process.
The regulatory environment has strong data protection requirements and zero tolerance for opaque or non-explainable decisions. Violations of GDPR can attract hefty penalties, such as in 2023, when approximately €2.1 billion in fines were imposed.
Region | Regulatory Focus | Primary Risk Drivers | Supervisory Expectations | Control Implications |
India | Context-aware, risk-tiered controls | Device reuse, SIM churn, mule layering | Real-time risk differentiation; adaptive controls | Continuous authentication, behavioral and device intelligence |
Southeast Asia | Identity continuity at scale | Fragmented ID systems, organized mule networks | Strong onboarding plus persistent monitoring | Cross-session identity linking and post-onboarding surveillance |
Middle East | Secure modernization of financial rails | Cross-border flows, rapid digitization | Crime controls that scale with payment speed and access | Real-time transaction monitoring and cross-border risk visibility |
European Union | Privacy, explainability, and accountability | Data misuse, opaque automation | Transparent, auditable decision-making | Explainable models, strict data governance, rights-preserving controls |
Best practices for KYC, AML, and FRM to adopt in 2026-27
Across regions, regulators are converging on the common principle that risk controls must be adaptive, continuous, and accountable.
How can businesses embrace these values for better KYC, AML, and FRM? These best practices show the way:
Move from document checks to identity assurance
Checklists confirm the existence of controls. Unfortunately, they do not confirm control.
Modern identity assurance treats trust as an ongoing state, not a one-time event. It continuously evaluates whether the same legitimate user remains in control of the account across sessions, devices, and behaviors.
This shift is critical for detecting account takeover, mule reuse, and synthetic identity abuse that documents alone cannot reveal.
Treat device intelligence as a first-class signal
Device intelligence is particularly necessary in environments where credentials are easily compromised or shared.
Devices carry more truth than credentials. They reveal certain traits that can be used to reveal underlying fraud patterns.
Often, without realizing, most users reveal:
Stability over time
Ownership patterns
Signs of manipulation or spoofing
Tracking and observing these signals are critical to identifying fraud signals before they snowball into full-sized catastrophes.

Use behavior to detect intent early
Fraud intent starts appearing way before fraud transactions happen. There are specific behavioral signals that, combined together, can help anticipate risk. These include:
Navigation patterns
Interaction timing
Environmental anomalies
These signals operate independently of transaction monitoring and provide an early-warning layer that traditional AML systems miss.
Connect identity across sessions and channels
Fraud rarely happens in isolation. It is usually orchestrated as part of a bigger plan, a sequence of events, and interdependent factors.
Attackers reuse devices, rotate credentials, and distribute activity across accounts and channels. Businesses that evaluate risk one session or one transaction at a time, miss the bigger picture.
Network-level intelligence which connects identities across time and touchpoints is far more effective than evaluating individuals in silos.

Reduce reliance on static rules
Static thresholds create blind spots, especially as attackers learn to operate just below them. Over time, rules accumulate, alerts increase, and effectiveness declines.
Modern risk programs rely on adaptive signals and decisioning frameworks that evolve with behavior, rather than chasing it.
Build explainable, auditable risk decisions
When fraud is discovered, knowing the cause and effect is insufficient. Businesses must dig deeper to understand the reason behind the fraud.
Unearthing the “why” behind the fraud will prove helpful in:
Regulatory audits
Internal governance
Cross-team trust
Clear decision flow such as the signals used, logic applied, outcome reached, and so forth, turns advanced risk intelligence into something regulators and executives can actually stand behind.
Related Read: Why the Future of Financial Crime Prevention Is Collaborative
Shift teams from alert handling to risk prevention
Smart security teams reduce operational burden by preventing risk earlier, rather than reacting to it later. This allows them to focus on control design, risk analysis, and continuous improvement, instead of manual firefighting.
The way forward: From compliance to confidence
KYC and AML remain essential foundations of trust and compliance. However, fraud risk management is the true differentiator.

Businesses that unify identity, device, behavior, and transaction intelligence move beyond just compliance to active risk prevention. They operate with the assurance that controls are effective, decisions are defensible, and customers are protected without unnecessary friction.
Modern risk management isn’t about more checks. It’s about making better decisions earlier, and with confidence.
Where Bureau fits in this FRM evolution
Bureau is built for businesses navigating the shift from procedural compliance to continuous, outcome-driven risk management. It acts as a unifying risk intelligence layer that connects identity, device, behavior, and transaction signals across the customer lifecycle.
By enabling context-aware decisioning, network-level visibility, and explainable risk outcomes, Bureau helps teams operationalize modern KYC, AML, and FRM principles without adding friction or complexity.
Move Beyond Compliance. Operate with Confidence.Discover how modern KYC, AML, and fraud risk teams are building adaptive, explainable, and continuous risk controls with Bureau. |
TABLE OF CONTENTS
See More
TABLE OF CONTENTS
See More
Recommended Blogs

Building Real-time Defenses in an Always-on Economy
In an always-on, connected economy, risks are created in real-time, rather than at discrete checkpoints. Defense strategies must, accordingly, level up to measure trust throughout the entire user experience, from first interaction to every single transaction. This always-on protection needs connected signals, adaptive decisioning, and protection that can keep pace with evolving digital behaviors and access methods.

iGaming KYC: Balancing Risk, Compliance, and Player Experience
KYC-driven identity verification is a core element for fraud prevention in iGaming. It helps these platforms establish trust at onboarding by creating a secure, fair, and sustainable ecosystem, preventing abuse, preserving integrity of the platform, and ensuring regulatory compliance.

How Device Intelligence Adapts to Global Data Sovereignty
Global data sovereignty laws are forcing financial institutions to rethink device intelligence, redesign fraud architecture, and operate compliant, real-time risk systems across increasingly fragmented regulatory environments. What this means in practice is a fundamental shift in how businesses design, deploy, and govern fraud systems across regions.
TABLE OF CONTENTS
See Less
TABLE OF CONTENTS
See Less



Solutions
Resources
© 2026 Bureau . All rights reserved.
Solutions
Solutions
Industries
Industries
Resources
Resources
Company
Company
Solutions
Solutions
Industries
Industries
Resources
Resources
Company
Company
© 2025 Bureau . All rights reserved. Privacy Policy. Terms of Service.
© 2025 Bureau . All rights reserved.
Privacy Policy. Terms of Service.
Follow Us
Leave behind fragmented tools. Stop fraud rings, cut false declines, and deliver secure digital journeys at scale
Our Presence
















Leave behind fragmented tools. Stop fraud rings, cut false declines, and deliver secure digital journeys at scale
Our Presence

















