Jan 12, 2026
Cloud Adoption in Financial Services: Risks, Reality, and What Comes Next
Cloud Adoption in Financial Services: Risks, Reality, and What Comes Next
Cloud Adoption in Financial Services: Risks, Reality, and What Comes Next
For financial services, the cloud isn’t a question of if, but how quickly. Real-time onboarding, payments, and credit evaluations require systems that can keep pace, which legacy platforms struggle to deliver. Because delayed fraud detection is no longer acceptable, the challenge for financial institutions is to move fast, while carefully managing risk.
Author
Team Bureau




TABLE OF CONTENTS
See Less
The financial services sector that creates and consumes, perhaps, the biggest volume and variety of data can be regarded as the ideal candidates for cloud adoption.
According to Gartner, by 2028 more than 50% of enterprises will use industry cloud platforms to accelerate their business initiatives.
Therefore, the question whether heavily-regulated financial institutions should adopt cloud or not, is not valid. The right question to ask is ‘how fast can they adapt without getting exposed to new risks?’
This is because, what is often left investigated is how these same drivers can also create new risk exposure.
Why financial services are accelerating cloud adoption
Cloud as a response to real-time financial journeys
Modern financial services operate in real time. Right from onboarding to payments and credit evaluations, cloud facilitates real-time financial journeys. However, legacy systems, designed for batch processing and with fixed capacity, struggle to keep up with these demands.
When transactions move in milliseconds, risk decisions cannot rely on after-the-fact controls.
Fraud and risk controls must operate at the same speed as these transactions. Delayed detection is no longer acceptable once funds move instantly.
API-driven ecosystems are now the default
Financial institutions no longer follow the traditional standalone island approach. Their closed systems have been replaced with open banking, embedded finance, and marketplace models. All these models primarily depend on APIs that banks, fintechs, merchants, and non-bank platforms use.
Each API expands the attack surface. Risk ownership becomes shared with little clarity over accountability. Fraud signals become scattered across partners, vendors, and platforms.
AI and fraud decisioning demand cloud-native compute
Fraud detection and risk scoring increasingly depend on machine learning models for data processing. Cloud provides the flexibility to deploy, iterate, and train these models.
However, as AI models influence decisions relating to approvals and rejections, data model governance takes the shape of a risk function, more than a data science concern. Poor signal quality, caused by biased or incomplete data, could scale bad decisions faster than before.
Distributed teams and always-on availability
Thanks to the cloud, financial services can now seamlessly operate across time zones, regions, and regulatory environments. Distributed engineering teams, faster recoveries, and business continuity are also the benefits that cloud promises.
That said, this always-on availability comes at the cost of maintaining uptime. Fraud incidents spike during outages, data/platform migrations, and failover events. There is the need to keep risk systems consistent even when infrastructure shifts.
Cloud modernization does not make risk disappear. It only eliminates old fraud models and introduces new risks that multiply, move faster, and become more interconnected across systems, vendors, and user journeys.
Cloud service models in financial services (and where risk lives)
Financial institutions do not rely on a single cloud model, but use a combination of SaaS, PaaS, and IaaS. Together they help fraud prevention, compliance, data analytics, and core systems maintenance. These models not only differ in their fundamental architecture, but also have varying risk ownership.
SaaS: speed with shared accountability
Software-as-a-Service is the most widely adopted cloud model in financial services. Banks and fintechs rely on SaaS tools for fraud detection, AML monitoring, compliance workflows, case management, and employee productivity.
PaaS: flexibility meets configuration risk
Platform-as-a-Service enables financial institutions to build and customize fraud logic, analytics pipelines, and integrations on managed cloud platforms. PaaS supports experimentation and advanced use cases, such as real-time risk scoring and AI-driven decisioning.
IaaS: control without intelligence is dangerous
Infrastructure-as-a-Service is used for core banking systems, disaster recovery, and large-scale data environments. IaaS provides maximum control over networks, storage, and compute resources.
Cloud models compared through a risk lens
Cloud model | Primary purpose | Key benefits | Where risk gaps emerge |
SaaS | Fraud tools, AML, compliance, productivity | Fast deployment, vendor-managed scaling | Fragmented visibility, black-box decisions, limited signal context |
PaaS | Custom fraud logic, analytics, AI workloads | Flexibility, rapid experimentation | Misconfiguration risk, model drift, governance gaps |
IaaS | Core systems, recovery, large data platforms | Full control, infrastructure resilience | Lack of unified intelligence, invisible fraud patterns |
The real challenge for financial institutions is not choosing the right cloud model. It is understanding why cloud adoption often exposes new risk gaps, even in well-architected environments.
Why cloud adoption often exposes new risk gaps
Cloud environments have all possible vulnerabilities plugged, which makes them secure by design. Most cloud providers also invest heavily in availability, baseline security controls, and compliance certifications to ensure ongoing security. Despite these efforts, many financial institutions report increased fraud exposure after cloud migration.
The reason is not the cloud itself. The issue is how risk intelligence is fragmented, governed, and applied across cloud environments.
Fragmented visibility across cloud environments
Cloud adoption spreads risk signals across systems and vendors that were never designed to work together. For instance, data could reside with one vendor while network control is with another. As a result, each system gets to own and see only part of the picture. There is no single system that can connect identity, behavior, and infrastructure risk in real-time.
Skills gaps become security gaps
For an elaborate security posture, security teams must understand signal intelligence, behavioral analysis, and device risk modeling. When these skills lag behind, security gaps emerge.
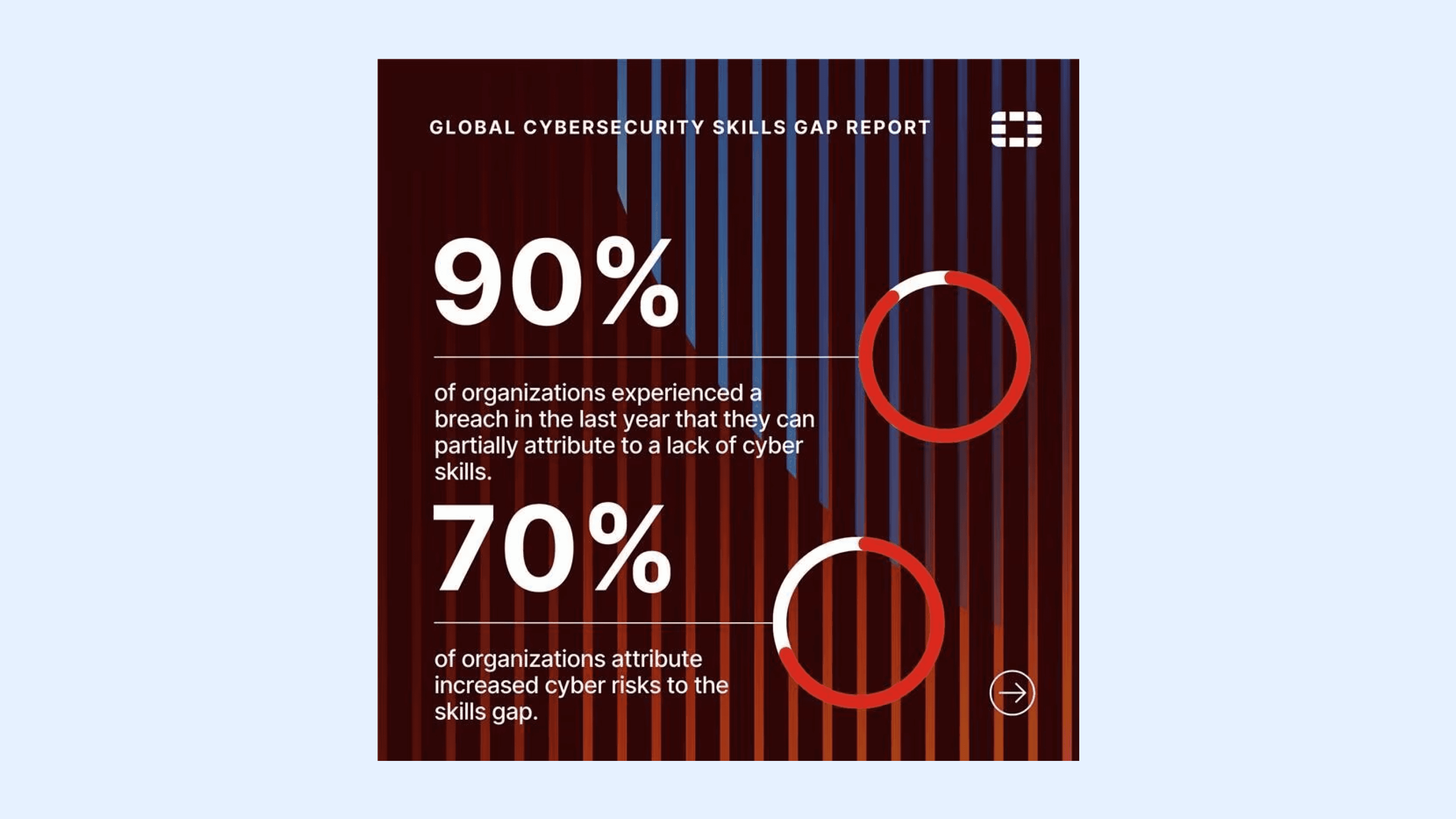
The World Economic Forum reports that 90% of organizations experienced a breach in the last year that can be partially attributed to a lack of cybersecurity skills.
Cloud scale amplifies fraud impact
Given the scale at which cloud operates and the future elasticity it provides, what starts as a small control gap can quickly become a systemic issue. Even the weakest link can be exploited across regions, devices, and accounts. Automated attacks reuse infrastructure, rotate identities, and adapt faster than manual controls can respond.
Why do these gaps persist?
These risk gaps persist because many institutions treat them as IT challenges and not risk intelligence challenges. They focus on tools, configurations, and vendors rather than intelligence flow.
Cloud adoption changes where data lives and how systems interact. Without a unified risk intelligence layer, visibility remains fragmented, skills gaps widen, and scale works in the attacker’s favor.
This is not a cloud failure. It is a risk intelligence challenge.
Cloud-native risk requires cloud-native intelligence
Cloud adoption changes how financial services build and scale systems. It must also change how risk is understood and managed.
Most traditional fraud and risk tools were designed for on-premise environments. They assumed stable identities, predictable infrastructure, and clear network perimeters. However, these assumptions no longer hold in cloud-based financial services.
In cloud environments, infrastructure is dynamic, identities rotate, and user journeys span multiple systems. Risk management must adapt to this reality.
For cloud-native risk management, the focus must shift from guarding boundaries to interpreting signals in motion.
Effective risk systems in the cloud share four characteristics:
Real-time: Decisions occur during the transaction, not after.
Context-aware: Signals are evaluated in relation to session, behavior, and history.
Signal-rich: Risk models draw from devices, networks, and behavioral patterns, not static identifiers alone.
Network-connected: Intelligence improves as patterns emerge across users, accounts, and environments.
This approach treats risk as a continuous state, and not a one-time checkpoint.
The two core pillars of cloud-native risk
As infrastructure becomes elastic and identities become transient, risk controls must anchor on what persists and adapts in real time. This requires two foundational pillars:
A financial risk model that scales with cloud speed, and
An intelligence layer that provides continuity across sessions, devices, and environments.
Financial risk management built for cloud scale
Cloud-native financial risk management operates across sessions and journeys rather than isolated events.
Instead of relying on static rules, it applies dynamic scoring that adjusts as behavior changes. Each interaction updates risk posture in real time, allowing institutions to approve, challenge, or block activity without interrupting legitimate users.
This model supports scale without sacrificing control. It allows financial platforms to respond instantly to emerging threats while maintaining low friction for trusted users.
Device intelligence as the missing control plane
In cloud environments, identities are fluid. Credentials pivot, accounts change, and users move across platforms. Devices, however, persist.
Device intelligence provides continuity where identity alone cannot.
It evaluates device trust, detects reuse across accounts, and identifies spoofing or emulation attempts. When connected to behavioral and network signals, devices become a stable anchor for risk assessment.
This control plane operates across cloud workflows, linking sessions that would otherwise appear unrelated. It allows risk teams to detect coordinated activity that bypasses identity-based controls.
How Bureau approaches cloud-native risk
Cloud adoption reshapes how financial services operate. Bureau understands that traditional risk models no longer align with this reality.
Rather than treating fraud, identity, and device risk as separate problems, Bureau approaches risk as a continuous intelligence layer that operates across modern cloud environments.
Cloud-first by design, not retrofitted
Bureau is built for cloud environments by design. It does not force legacy, perimeter-based assumptions to adapt to dynamic systems.
This design choice matters. Cloud-native systems demand real-time decisioning, elastic scale, and resilience across distributed workflows. Bureau aligns to these requirements by default, rather than compensating for them later.
Unified risk decisioning across signals
Bureau brings multiple risk signals into a single decisioning layer. This reduces fragmentation and improves context at the moment of action.
Device intelligence: Establishes continuity across sessions, accounts, and platforms, even when identities change.
Behavioral analytics: Interprets how users interact, not just who they claim to be.
Transaction and session risk: Evaluates financial activity within its behavioral and device context, not in isolation.
Together, these signals support decisions that reflect how fraud actually operates in cloud environments.
Designed for SaaS, PaaS, and IaaS environments
Bureau operates across mixed cloud models without forcing architectural change.
It integrates into SaaS workflows, supports custom logic in PaaS environments, and extends visibility within IaaS deployments.
This flexibility reflects how financial institutions actually run their systems today. Risk intelligence remains consistent, even when infrastructure is not.
Outcomes that align with cloud realities
Bureau’s approach supports outcomes that matter to risk and technology leaders.
Detect fraud earlier: By identifying patterns that emerge across devices, sessions, and networks.
Reduce false positives: By adding context instead of tightening rules.
Maintain resilience without friction: By adapting risk responses in real time rather than interrupting users.
These outcomes follow from better intelligence, not heavier controls.
In a nutshell
Cloud adoption in financial services is no longer optional. It is a structural shift driven by real-time products, open ecosystems, and AI-led decisioning.
This shift does not eliminate risk. It changes how risk forms, spreads, and scales. Fragmented signals, fluid identities, and automated attacks expose the limits of legacy risk models built for static systems.
Cloud-native financial services need cloud-native risk intelligence. Risk systems must operate in real time, connect context across environments, and adapt as behavior changes. Only then can institutions scale trust without slowing growth.
Cloud adoption changes how financial services operate. Risk intelligence must change how trust is built.
Explore how Bureau’s cloud-native FRM adapts to modern risk.
The financial services sector that creates and consumes, perhaps, the biggest volume and variety of data can be regarded as the ideal candidates for cloud adoption.
According to Gartner, by 2028 more than 50% of enterprises will use industry cloud platforms to accelerate their business initiatives.
Therefore, the question whether heavily-regulated financial institutions should adopt cloud or not, is not valid. The right question to ask is ‘how fast can they adapt without getting exposed to new risks?’
This is because, what is often left investigated is how these same drivers can also create new risk exposure.

Why financial services are accelerating cloud adoption
Cloud as a response to real-time financial journeys
Modern financial services operate in real time. Right from onboarding to payments and credit evaluations, cloud facilitates real-time financial journeys. However, legacy systems, designed for batch processing and with fixed capacity, struggle to keep up with these demands.
When transactions move in milliseconds, risk decisions cannot rely on after-the-fact controls.
Fraud and risk controls must operate at the same speed as these transactions. Delayed detection is no longer acceptable once funds move instantly.
API-driven ecosystems are now the default
Financial institutions no longer follow the traditional standalone island approach. Their closed systems have been replaced with open banking, embedded finance, and marketplace models. All these models primarily depend on APIs that banks, fintechs, merchants, and non-bank platforms use.
Each API expands the attack surface. Risk ownership becomes shared with little clarity over accountability. Fraud signals become scattered across partners, vendors, and platforms.

AI and fraud decisioning demand cloud-native compute
Fraud detection and risk scoring increasingly depend on machine learning models for data processing. Cloud provides the flexibility to deploy, iterate, and train these models.
However, as AI models influence decisions relating to approvals and rejections, data model governance takes the shape of a risk function, more than a data science concern. Poor signal quality, caused by biased or incomplete data, could scale bad decisions faster than before.
Distributed teams and always-on availability
Thanks to the cloud, financial services can now seamlessly operate across time zones, regions, and regulatory environments. Distributed engineering teams, faster recoveries, and business continuity are also the benefits that cloud promises.
That said, this always-on availability comes at the cost of maintaining uptime. Fraud incidents spike during outages, data/platform migrations, and failover events. There is the need to keep risk systems consistent even when infrastructure shifts.
Cloud modernization does not make risk disappear. It only eliminates old fraud models and introduces new risks that multiply, move faster, and become more interconnected across systems, vendors, and user journeys.
Cloud service models in financial services (and where risk lives)
Financial institutions do not rely on a single cloud model, but use a combination of SaaS, PaaS, and IaaS. Together they help fraud prevention, compliance, data analytics, and core systems maintenance. These models not only differ in their fundamental architecture, but also have varying risk ownership.

SaaS: speed with shared accountability
Software-as-a-Service is the most widely adopted cloud model in financial services. Banks and fintechs rely on SaaS tools for fraud detection, AML monitoring, compliance workflows, case management, and employee productivity.
PaaS: flexibility meets configuration risk
Platform-as-a-Service enables financial institutions to build and customize fraud logic, analytics pipelines, and integrations on managed cloud platforms. PaaS supports experimentation and advanced use cases, such as real-time risk scoring and AI-driven decisioning.
IaaS: control without intelligence is dangerous
Infrastructure-as-a-Service is used for core banking systems, disaster recovery, and large-scale data environments. IaaS provides maximum control over networks, storage, and compute resources.
Cloud models compared through a risk lens
Cloud model | Primary purpose | Key benefits | Where risk gaps emerge |
SaaS | Fraud tools, AML, compliance, productivity | Fast deployment, vendor-managed scaling | Fragmented visibility, black-box decisions, limited signal context |
PaaS | Custom fraud logic, analytics, AI workloads | Flexibility, rapid experimentation | Misconfiguration risk, model drift, governance gaps |
IaaS | Core systems, recovery, large data platforms | Full control, infrastructure resilience | Lack of unified intelligence, invisible fraud patterns |
The real challenge for financial institutions is not choosing the right cloud model. It is understanding why cloud adoption often exposes new risk gaps, even in well-architected environments.
Why cloud adoption often exposes new risk gaps
Cloud environments have all possible vulnerabilities plugged, which makes them secure by design. Most cloud providers also invest heavily in availability, baseline security controls, and compliance certifications to ensure ongoing security. Despite these efforts, many financial institutions report increased fraud exposure after cloud migration.
The reason is not the cloud itself. The issue is how risk intelligence is fragmented, governed, and applied across cloud environments.
Fragmented visibility across cloud environments
Cloud adoption spreads risk signals across systems and vendors that were never designed to work together. For instance, data could reside with one vendor while network control is with another. As a result, each system gets to own and see only part of the picture. There is no single system that can connect identity, behavior, and infrastructure risk in real-time.
Skills gaps become security gaps
For an elaborate security posture, security teams must understand signal intelligence, behavioral analysis, and device risk modeling. When these skills lag behind, security gaps emerge.
The World Economic Forum reports that 90% of organizations experienced a breach in the last year that can be partially attributed to a lack of cybersecurity skills.

Cloud scale amplifies fraud impact
Given the scale at which cloud operates and the future elasticity it provides, what starts as a small control gap can quickly become a systemic issue. Even the weakest link can be exploited across regions, devices, and accounts. Automated attacks reuse infrastructure, rotate identities, and adapt faster than manual controls can respond.
Why do these gaps persist?
These risk gaps persist because many institutions treat them as IT challenges and not risk intelligence challenges. They focus on tools, configurations, and vendors rather than intelligence flow.
Cloud adoption changes where data lives and how systems interact. Without a unified risk intelligence layer, visibility remains fragmented, skills gaps widen, and scale works in the attacker’s favor.
This is not a cloud failure. It is a risk intelligence challenge.
Cloud-native risk requires cloud-native intelligence
Cloud adoption changes how financial services build and scale systems. It must also change how risk is understood and managed.
Most traditional fraud and risk tools were designed for on-premise environments. They assumed stable identities, predictable infrastructure, and clear network perimeters. However, these assumptions no longer hold in cloud-based financial services.
In cloud environments, infrastructure is dynamic, identities rotate, and user journeys span multiple systems. Risk management must adapt to this reality.
For cloud-native risk management, the focus must shift from guarding boundaries to interpreting signals in motion.
Effective risk systems in the cloud share four characteristics:
Real-time: Decisions occur during the transaction, not after.
Context-aware: Signals are evaluated in relation to session, behavior, and history.
Signal-rich: Risk models draw from devices, networks, and behavioral patterns, not static identifiers alone.
Network-connected: Intelligence improves as patterns emerge across users, accounts, and environments.
This approach treats risk as a continuous state, and not a one-time checkpoint.
The two core pillars of cloud-native risk
As infrastructure becomes elastic and identities become transient, risk controls must anchor on what persists and adapts in real time. This requires two foundational pillars:
A financial risk model that scales with cloud speed, and
An intelligence layer that provides continuity across sessions, devices, and environments.
Financial risk management built for cloud scale
Cloud-native financial risk management operates across sessions and journeys rather than isolated events.
Instead of relying on static rules, it applies dynamic scoring that adjusts as behavior changes. Each interaction updates risk posture in real time, allowing institutions to approve, challenge, or block activity without interrupting legitimate users.
This model supports scale without sacrificing control. It allows financial platforms to respond instantly to emerging threats while maintaining low friction for trusted users.
Device intelligence as the missing control plane
In cloud environments, identities are fluid. Credentials pivot, accounts change, and users move across platforms. Devices, however, persist.
Device intelligence provides continuity where identity alone cannot.
It evaluates device trust, detects reuse across accounts, and identifies spoofing or emulation attempts. When connected to behavioral and network signals, devices become a stable anchor for risk assessment.
This control plane operates across cloud workflows, linking sessions that would otherwise appear unrelated. It allows risk teams to detect coordinated activity that bypasses identity-based controls.

How Bureau approaches cloud-native risk
Cloud adoption reshapes how financial services operate. Bureau understands that traditional risk models no longer align with this reality.
Rather than treating fraud, identity, and device risk as separate problems, Bureau approaches risk as a continuous intelligence layer that operates across modern cloud environments.
Cloud-first by design, not retrofitted
Bureau is built for cloud environments by design. It does not force legacy, perimeter-based assumptions to adapt to dynamic systems.
This design choice matters. Cloud-native systems demand real-time decisioning, elastic scale, and resilience across distributed workflows. Bureau aligns to these requirements by default, rather than compensating for them later.
Unified risk decisioning across signals
Bureau brings multiple risk signals into a single decisioning layer. This reduces fragmentation and improves context at the moment of action.
Device intelligence: Establishes continuity across sessions, accounts, and platforms, even when identities change.
Behavioral analytics: Interprets how users interact, not just who they claim to be.
Transaction and session risk: Evaluates financial activity within its behavioral and device context, not in isolation.
Together, these signals support decisions that reflect how fraud actually operates in cloud environments.
Designed for SaaS, PaaS, and IaaS environments
Bureau operates across mixed cloud models without forcing architectural change.
It integrates into SaaS workflows, supports custom logic in PaaS environments, and extends visibility within IaaS deployments.
This flexibility reflects how financial institutions actually run their systems today. Risk intelligence remains consistent, even when infrastructure is not.
Outcomes that align with cloud realities
Bureau’s approach supports outcomes that matter to risk and technology leaders.
Detect fraud earlier: By identifying patterns that emerge across devices, sessions, and networks.
Reduce false positives: By adding context instead of tightening rules.
Maintain resilience without friction: By adapting risk responses in real time rather than interrupting users.
These outcomes follow from better intelligence, not heavier controls.
In a nutshell
Cloud adoption in financial services is no longer optional. It is a structural shift driven by real-time products, open ecosystems, and AI-led decisioning.
This shift does not eliminate risk. It changes how risk forms, spreads, and scales. Fragmented signals, fluid identities, and automated attacks expose the limits of legacy risk models built for static systems.
Cloud-native financial services need cloud-native risk intelligence. Risk systems must operate in real time, connect context across environments, and adapt as behavior changes. Only then can institutions scale trust without slowing growth.
Cloud adoption changes how financial services operate. Risk intelligence must change how trust is built.
Explore how Bureau’s cloud-native FRM adapts to modern risk.
TABLE OF CONTENTS
See More
TABLE OF CONTENTS
See More
Recommended Blogs

Building Real-time Defenses in an Always-on Economy
In an always-on, connected economy, risks are created in real-time, rather than at discrete checkpoints. Defense strategies must, accordingly, level up to measure trust throughout the entire user experience, from first interaction to every single transaction. This always-on protection needs connected signals, adaptive decisioning, and protection that can keep pace with evolving digital behaviors and access methods.

iGaming KYC: Balancing Risk, Compliance, and Player Experience
KYC-driven identity verification is a core element for fraud prevention in iGaming. It helps these platforms establish trust at onboarding by creating a secure, fair, and sustainable ecosystem, preventing abuse, preserving integrity of the platform, and ensuring regulatory compliance.

How Device Intelligence Adapts to Global Data Sovereignty
Global data sovereignty laws are forcing financial institutions to rethink device intelligence, redesign fraud architecture, and operate compliant, real-time risk systems across increasingly fragmented regulatory environments. What this means in practice is a fundamental shift in how businesses design, deploy, and govern fraud systems across regions.
TABLE OF CONTENTS
See Less
TABLE OF CONTENTS
See Less



Solutions
Resources
© 2026 Bureau . All rights reserved.
Solutions
Solutions
Industries
Industries
Resources
Resources
Company
Company
Solutions
Solutions
Industries
Industries
Resources
Resources
Company
Company
© 2025 Bureau . All rights reserved. Privacy Policy. Terms of Service.
© 2025 Bureau . All rights reserved.
Privacy Policy. Terms of Service.
Follow Us
Leave behind fragmented tools. Stop fraud rings, cut false declines, and deliver secure digital journeys at scale
Our Presence
















Leave behind fragmented tools. Stop fraud rings, cut false declines, and deliver secure digital journeys at scale
Our Presence

















