Dec 12, 2025
Fraudulent Transactions: Behavioral Red Flags Commonly Ignored
Fraudulent Transactions: Behavioral Red Flags Commonly Ignored
Fraudulent Transactions: Behavioral Red Flags Commonly Ignored
Fraudulent transactions rarely occur without subtle behavioral anomalies. Ignoring these warning signals can result in substantial financial and reputational losses. By monitoring and acting on behavioral red flags, businesses can quickly deter fraud and maintain seamless user experience.
Author
Team Bureau



TABLE OF CONTENTS
See Less
Subtle signals such as sudden device changes, rapid bursts of transactions, inconsistent login behavior, or cross-channel inconsistencies, often precede fraudulent activities, and are overlooked. Fraudsters exploit these gaps to act quickly before businesses can connect the dots.
These small anomalies may not appear significant when viewed in isolation, but when accumulated, they can compromise the entire business system. As a result, businesses that monitor signals in silos rather than correlating them in real-time, are at a greater risk of exposure.

Why behavioral signals matter
Digital fraud is evolving faster than businesses can catch up. Using latest technologies like generative AI, deepfakes, and automation at scale, fraudsters exploit minute inconsistencies in user behavior, including: shifts in device use, evolving navigation patterns, and changes in transaction timing. Although these behavioral signals can provide some of the earliest indications of potential fraud, they are often overlooked.
TransUnion’s 2025 State of Omnichannel Fraud Report found that 53% of consumers were targeted by digital fraud attempts in the past year, with phishing, smishing, and vishing among the most common tactics. Simultaneously, data breaches exposed record volumes of sensitive information, creating fertile ground for downstream fraud.
Similarly, Experian’s 2024 Future of Fraud Forecast predicts a surge in synthetic identity fraud and AI-powered scams, highlighting attackers’ growing sophistication in mimicking human behavior to bypass conventional security measures.
Therefore, relying solely on identity-based checks is no longer sufficient. To stay ahead, businesses must closely observe how customers behave in real time, rather than just who they are.
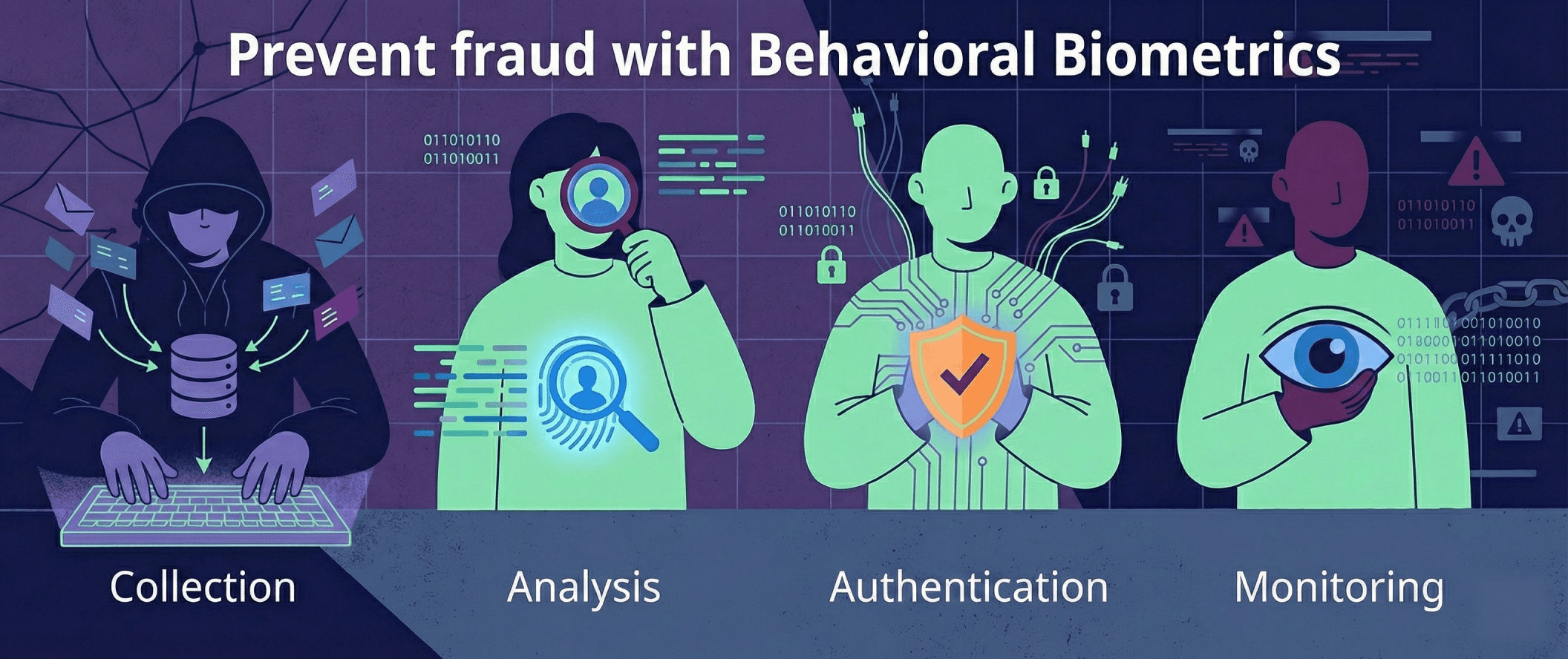
Five common behavioral red flags often ignored
The five most common behavioral red flags that businesses often fail to recognize or ignore include:
New or high-risk device usage: One of the earliest indicators of fraud is device-related anomalies, as fraudsters frequently cycle through devices and proxies to test stolen credentials. A customer who typically logs in via mobile may suddenly appear on a desktop from a distant location, or a device linked to multiple suspicious accounts might attempt access. Recognizing such unusual or high-risk devices early allows businesses to prevent fraudulent activity before any financial damage can occur.
Suspicious email or account age: Legitimate users have emails with an established history and consistent usage, whereas fraudsters often rely on newly created or disposable email addresses. Accounts associated with throwaway emails, especially those used across multiple transactions, are a significant red flag. Similarly, detecting young or suspiciously structured accounts early is essential to mitigating risk. Experian’s 2024 report, mentioned earlier, highlights “bust-out” fraud, in which synthetic identities are gradually built before fraudsters cash out in rapid bursts.
Rapid transactions: Velocity anomalies occur when accounts suddenly engage in multiple high-value transactions within a short period. For instance, a dormant account may suddenly attempt several transfers within minutes, or a new customer might max out credit limits immediately. Such rapid bursts are hallmark patterns of fraud, indicating that a fraudster is acting quickly to exploit the account before detection systems can respond.
Authentication and navigation anomalies: Repeated failed logins followed by a sudden success can indicate automated attacks or credential stuffing. Similarly, navigation patterns, such as form filling at machine speed, skipping expected steps, or accessing unusual sections of an application, often signals scripted behavior. These indicators provide insights into what a user does, as well as how they do it, offering a high-value lens to differentiate legitimate customers from fraudsters.
Cross-channel inconsistency: Fraud today is omnichannel, with attackers exploiting whichever channel is the weakest. A user, who usually transacts via mobile, may suddenly attempt a high-value purchase on desktop, or an account may abruptly interact through a call center. Ignoring these inconsistencies can leave businesses vulnerable to sophisticated account takeovers and other scams.
Why businesses overlook red flags
Despite knowing the importance of early detection for effective fraud prevention, many businesses frequently overlook behavioral signals indicative of fraud. Several factors contribute to this:
Data silos: Fraud, risk, and customer experience teams usually operate separately. This prevents the business from getting a complete picture of user behavior.
Fear of false positives: Businesses worry that adding friction may inconvenience legitimate customers, and may set lenient detection thresholds.
Legacy systems: Many fraud detection solutions cannot integrate multiple real-time signals effectively, leaving valuable data unused.
Traditional checks: Most businesses still rely on traditional identity checks, thereby missing the behavioral context for effective fraud prevention.
Slow adaptation: While fraud tactics are evolving rapidly, many businesses are slow to implement adaptive countermeasures and continue to rely on legacy fraud defense mechanisms.
How to identify behavioral red flags without compromising UX
To balance fraud prevention with a positive user experience, businesses must undertake layered monitoring and proactive measures, such as those described below:
🚩 Capture comprehensive telemetry: Monitor device fingerprints, IP addresses, login times, and navigation sequences across all user interactions.
🚩 Integrate signals into contextual risk scores: Rather than using single signals as hard stops, combine device, account age, velocity, and authentication anomalies into composite scores for better risk assessment.
🚩 Apply adaptive friction: To intercept fraud with minimum disruption to genuine users, introduce step-up authentication only when risk scores exceed predefined thresholds.
🚩 Share intelligence: Participation in industry consortia and graph networks enables businesses to detect reused devices, synthetic identities, and mule accounts.
🚩 Define normal customer behavior: Baseline standard behaviors to understand each user’s typical actions and flag sharp deviations indicative of potential fraud.
Bureau’s multi-layered approach to fraud prevention
Fraudulent transactions are often preceded by subtle behavioral anomalies that businesses fail to detect. With digital fraud becoming more sophisticated, monitoring behavioral indicators is no longer optional. Bureau’s multi-layered fraud prevention approach empowers businesses to detect and act on behavioral red flags in real-time, significantly reducing risk while also maintaining seamless user experience.
Bureau’s unified risk decisioning platform integrates more than 200 digital signals, including device intelligence, behavioral patterns, account age, transaction velocity, and historical linkages to intercept fraud before it can escalate.
Unlike traditional, reactive solutions, Bureau’s adaptive, risk-based authentication, reduces false positives, protecting both revenue and customer trust.
See how Bureau identifies and acts on subtle behavioral anomalies to deter fraud in real-time, book a free demo now.
Quick checklist for fraud prevention
Track device and session telemetry at every touchpoint.
Identify accounts with new or disposable email domains.
Monitor transaction velocity and unusual deviations.
Analyze navigation and login behaviors for anomalies.
Compare behavior across mobile, web, and other channels.
Subtle signals such as sudden device changes, rapid bursts of transactions, inconsistent login behavior, or cross-channel inconsistencies, often precede fraudulent activities, and are overlooked. Fraudsters exploit these gaps to act quickly before businesses can connect the dots.
These small anomalies may not appear significant when viewed in isolation, but when accumulated, they can compromise the entire business system. As a result, businesses that monitor signals in silos rather than correlating them in real-time, are at a greater risk of exposure.

Why behavioral signals matter
Digital fraud is evolving faster than businesses can catch up. Using latest technologies like generative AI, deepfakes, and automation at scale, fraudsters exploit minute inconsistencies in user behavior, including: shifts in device use, evolving navigation patterns, and changes in transaction timing. Although these behavioral signals can provide some of the earliest indications of potential fraud, they are often overlooked.
TransUnion’s 2025 State of Omnichannel Fraud Report found that 53% of consumers were targeted by digital fraud attempts in the past year, with phishing, smishing, and vishing among the most common tactics. Simultaneously, data breaches exposed record volumes of sensitive information, creating fertile ground for downstream fraud.
Similarly, Experian’s 2024 Future of Fraud Forecast predicts a surge in synthetic identity fraud and AI-powered scams, highlighting attackers’ growing sophistication in mimicking human behavior to bypass conventional security measures.
Therefore, relying solely on identity-based checks is no longer sufficient. To stay ahead, businesses must closely observe how customers behave in real time, rather than just who they are.

Five common behavioral red flags often ignored
The five most common behavioral red flags that businesses often fail to recognize or ignore include:
New or high-risk device usage: One of the earliest indicators of fraud is device-related anomalies, as fraudsters frequently cycle through devices and proxies to test stolen credentials. A customer who typically logs in via mobile may suddenly appear on a desktop from a distant location, or a device linked to multiple suspicious accounts might attempt access. Recognizing such unusual or high-risk devices early allows businesses to prevent fraudulent activity before any financial damage can occur.
Suspicious email or account age: Legitimate users have emails with an established history and consistent usage, whereas fraudsters often rely on newly created or disposable email addresses. Accounts associated with throwaway emails, especially those used across multiple transactions, are a significant red flag. Similarly, detecting young or suspiciously structured accounts early is essential to mitigating risk. Experian’s 2024 report, mentioned earlier, highlights “bust-out” fraud, in which synthetic identities are gradually built before fraudsters cash out in rapid bursts.
Rapid transactions: Velocity anomalies occur when accounts suddenly engage in multiple high-value transactions within a short period. For instance, a dormant account may suddenly attempt several transfers within minutes, or a new customer might max out credit limits immediately. Such rapid bursts are hallmark patterns of fraud, indicating that a fraudster is acting quickly to exploit the account before detection systems can respond.
Authentication and navigation anomalies: Repeated failed logins followed by a sudden success can indicate automated attacks or credential stuffing. Similarly, navigation patterns, such as form filling at machine speed, skipping expected steps, or accessing unusual sections of an application, often signals scripted behavior. These indicators provide insights into what a user does, as well as how they do it, offering a high-value lens to differentiate legitimate customers from fraudsters.
Cross-channel inconsistency: Fraud today is omnichannel, with attackers exploiting whichever channel is the weakest. A user, who usually transacts via mobile, may suddenly attempt a high-value purchase on desktop, or an account may abruptly interact through a call center. Ignoring these inconsistencies can leave businesses vulnerable to sophisticated account takeovers and other scams.
Why businesses overlook red flags
Despite knowing the importance of early detection for effective fraud prevention, many businesses frequently overlook behavioral signals indicative of fraud. Several factors contribute to this:
Data silos: Fraud, risk, and customer experience teams usually operate separately. This prevents the business from getting a complete picture of user behavior.
Fear of false positives: Businesses worry that adding friction may inconvenience legitimate customers, and may set lenient detection thresholds.
Legacy systems: Many fraud detection solutions cannot integrate multiple real-time signals effectively, leaving valuable data unused.
Traditional checks: Most businesses still rely on traditional identity checks, thereby missing the behavioral context for effective fraud prevention.
Slow adaptation: While fraud tactics are evolving rapidly, many businesses are slow to implement adaptive countermeasures and continue to rely on legacy fraud defense mechanisms.
How to identify behavioral red flags without compromising UX
To balance fraud prevention with a positive user experience, businesses must undertake layered monitoring and proactive measures, such as those described below:
🚩 Capture comprehensive telemetry: Monitor device fingerprints, IP addresses, login times, and navigation sequences across all user interactions.
🚩 Integrate signals into contextual risk scores: Rather than using single signals as hard stops, combine device, account age, velocity, and authentication anomalies into composite scores for better risk assessment.
🚩 Apply adaptive friction: To intercept fraud with minimum disruption to genuine users, introduce step-up authentication only when risk scores exceed predefined thresholds.
🚩 Share intelligence: Participation in industry consortia and graph networks enables businesses to detect reused devices, synthetic identities, and mule accounts.
🚩 Define normal customer behavior: Baseline standard behaviors to understand each user’s typical actions and flag sharp deviations indicative of potential fraud.
Bureau’s multi-layered approach to fraud prevention
Fraudulent transactions are often preceded by subtle behavioral anomalies that businesses fail to detect. With digital fraud becoming more sophisticated, monitoring behavioral indicators is no longer optional. Bureau’s multi-layered fraud prevention approach empowers businesses to detect and act on behavioral red flags in real-time, significantly reducing risk while also maintaining seamless user experience.
Bureau’s unified risk decisioning platform integrates more than 200 digital signals, including device intelligence, behavioral patterns, account age, transaction velocity, and historical linkages to intercept fraud before it can escalate.
Unlike traditional, reactive solutions, Bureau’s adaptive, risk-based authentication, reduces false positives, protecting both revenue and customer trust.
See how Bureau identifies and acts on subtle behavioral anomalies to deter fraud in real-time, book a free demo now.
Quick checklist for fraud prevention
Track device and session telemetry at every touchpoint.
Identify accounts with new or disposable email domains.
Monitor transaction velocity and unusual deviations.
Analyze navigation and login behaviors for anomalies.
Compare behavior across mobile, web, and other channels.
TABLE OF CONTENTS
See More
Recommended Blogs

How Middle East Banks Can Rethink Fraud Prevention
Rapid digital adoption is reshaping banking across the Middle East. Instant onboarding, digital wallets, and super apps are now the norm, expanding the attack surface in the process. To deliver strong protection without adding friction, banks in the region must counter AI-driven fraud with connected intelligence across identity, devices, and behavior.

Building Real-time Defenses in an Always-on Economy
In an always-on, connected economy, risks are created in real-time, rather than at discrete checkpoints. Defense strategies must, accordingly, level up to measure trust throughout the entire user experience, from first interaction to every single transaction. This always-on protection needs connected signals, adaptive decisioning, and protection that can keep pace with evolving digital behaviors and access methods.

iGaming KYC: Balancing Risk, Compliance, and Player Experience
KYC-driven identity verification is a core element for fraud prevention in iGaming. It helps these platforms establish trust at onboarding by creating a secure, fair, and sustainable ecosystem, preventing abuse, preserving integrity of the platform, and ensuring regulatory compliance.
TABLE OF CONTENTS
See Less


Solutions
Resources
© 2026 Bureau . All rights reserved.
Solutions
Industries
Resources
Company
Solutions
Industries
Resources
Company
© 2026 Bureau . All rights reserved.
Follow Us
Leave behind fragmented tools. Stop fraud rings, cut false declines, and deliver secure digital journeys at scale
Our Presence












Leave behind fragmented tools. Stop fraud rings, cut false declines, and deliver secure digital journeys at scale
Our Presence












© 2026 Bureau . All rights reserved.

