Jan 7, 2026
How Enterprises Can Defend Against Networked, Industrial-Scale Fraud
How Enterprises Can Defend Against Networked, Industrial-Scale Fraud
How Enterprises Can Defend Against Networked, Industrial-Scale Fraud
Fraud is becoming increasingly sophisticated and networked. However, while fraudsters are hyper-connected, the businesses defending against them remain largely siloed. The only way to dismantle networked fraud rings is through cross-industry intelligence and unified risk decisioning.
Author
Vishwas Mysore




TABLE OF CONTENTS
See Less
Globally, people and businesses are losing money to organized fraud rings and networks from account takeovers, promo abuse and chargeback fraud. The FBI and Internet Crime Complaint Center (IC3) have issued several public service announcements (such as this) regarding evolving cyber threats and financial crimes, especially during the holiday season, where people are prone to losing money to fraudsters, often a part of large scale criminal rings and networks.
The rising tide of scams has also led the FBI to launch the TakeABeat campaign - a public awareness initiative to ensure people remain safe from fraud.
Fraud is becoming increasingly sophisticated and networked. While device networks may be local or trans-national, fraudsters are leveraging criminal toolkits comprising AI, deepfakes, and generative AI to automate and scale fraud. These tools help criminals make fraud schemes more believable and allow smaller rings to operate like massive organizations.
Related Read: A Food Delivery Company Eliminates a 2,700+ User Fraud Ring
“Fraudsters are networking, Are businesses too?” This is not just a catchy line that has caught the attention of bankers, financial institutions, and online marketplaces alike, but indeed a hardhitting fact revealed by several investigations.
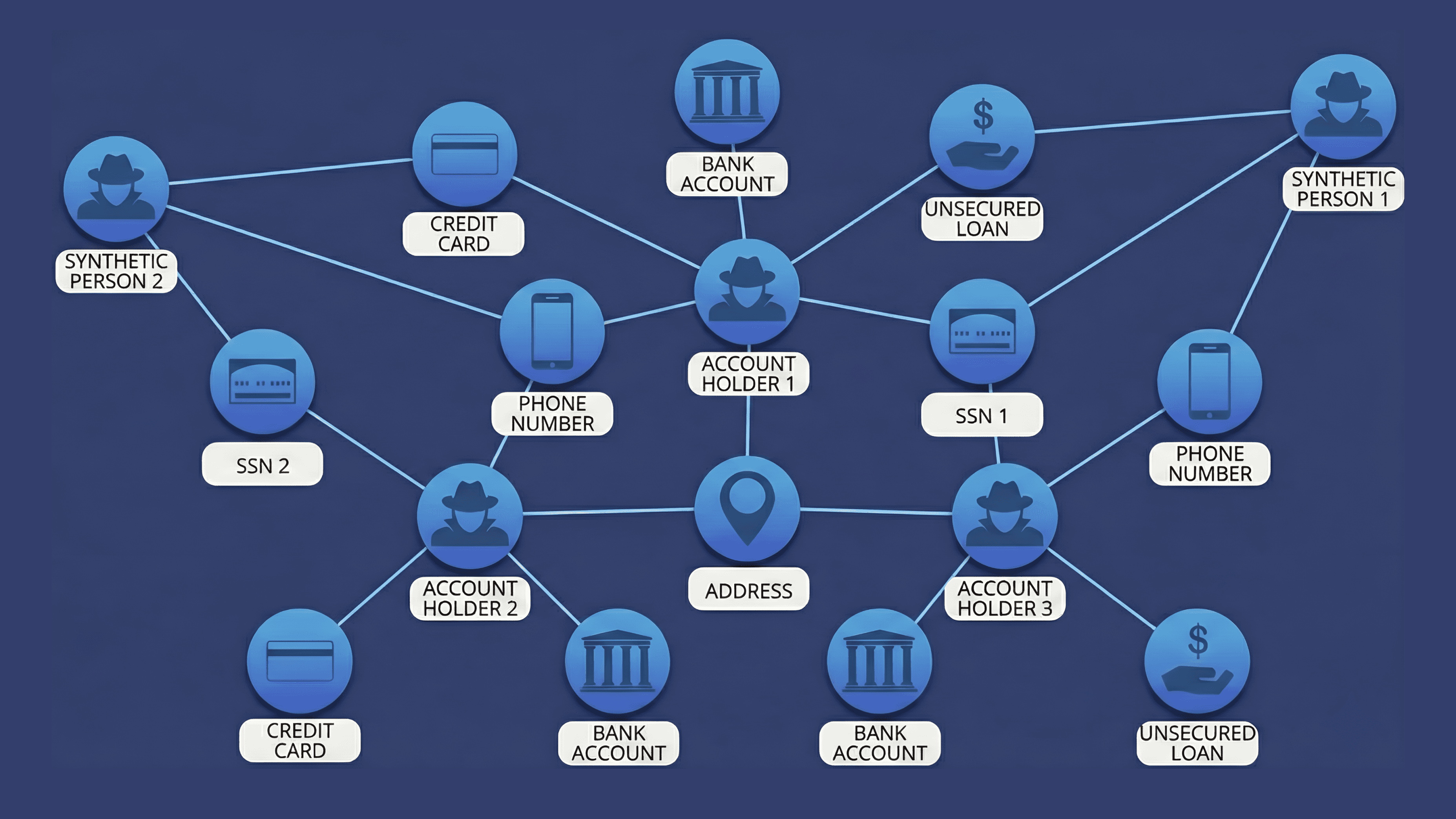
How fraudsters use networked infrastructure and tools
Fraudsters use centralized "farms" and automated networks to scale attacks that would be impossible for single individuals. These often include:
Device Farms: Collections of physical smartphones or virtual emulators that simulate thousands of "unique" users from a single location. These are used to bypass device-based limits for sign-up bonuses and referral rewards.
Botnets and Automated Scripts: Networks of hijacked or automated accounts that perform "credential stuffing" to take over accounts en masse. AI-driven bots are now increasingly being used to automate multi-stage attacks and simulate legitimate user engagement.
SIM Banks: Groups of devices used to bypass SMS-based two-factor authentication (2FA). They manage thousands of virtual or physical phone numbers for mass account verification.
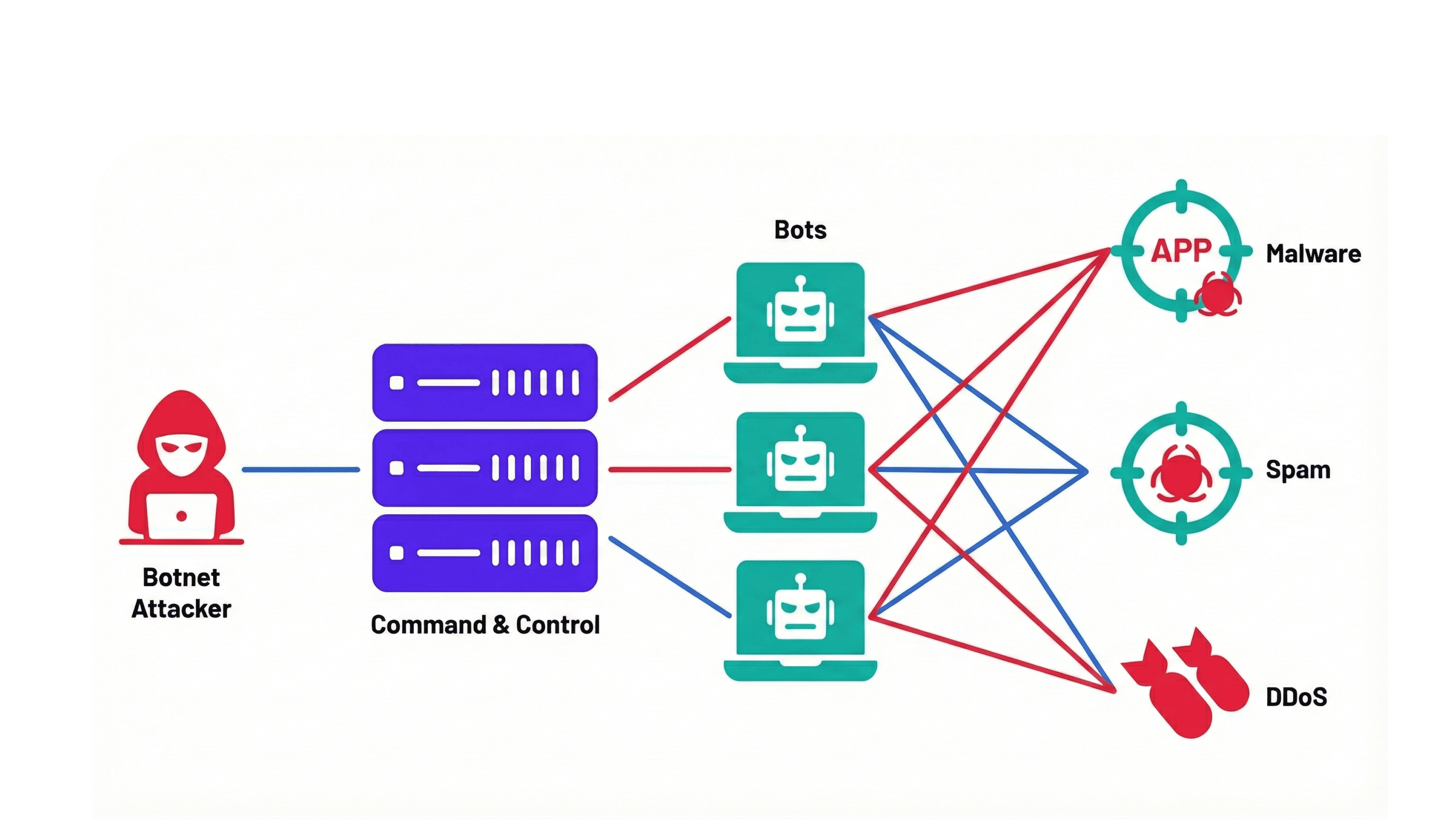
Coordination among fraud rings
As has emerged from multiple investigations across markets, fraud today is a highly organized, professionalized "business" model. And fraudsters operate as coordinated syndicates that mimic legitimate corporate structures with:.
Specialized Roles: Much like a tech startup, fraud rings have "departmental" roles, some members focus on data harvesting (phishing), others on money laundering (mules), and some on technical evasion (spoofing devices).
Infrastructure Sharing: These networks share "fraud-as-a-service" toolkits, including jailbroken devices, proxy IPs, and virtual SIMs, allowing them to scale attacks rapidly across multiple platforms.
Cross-platform Probing: Rings often "poke" a system to find a vulnerability. Once a weakness is found in one bank or marketplace, the entire network is alerted to exploit the same gap across other institutions with similar profiles.
Related Read: What are Money Mules
The common modus operandi of a fraud ring includes:
Collusion Loops: Networks where "buyers" and "sellers" in marketplaces coordinate fake transactions to trigger referral payouts and sign-up credits.
Multi-stage Operations: Account takeover is often just the "entry point." Once a network gains access to legitimate accounts, they are used to farm loyalty points, distribute malware, or conduct larger financial transfers to "mule networks".
Identity Harvesting: Rings use stolen data from past breaches to create "synthetic identities", combinations of real and fake data, to bypass identity verification processes (KYC) at scale.
Indicators of networked activity
Security systems detect networked fraud by identifying clusters of behavior that lack typical human randomness. Some common telltales include:
Proximity-based Anomalies: Clusters of hundreds of "unique" devices operating from the same precise physical location; a hallmark of a physical device farm.
High Device-to-Account Ratios: Multiple accounts (often hundreds) being accessed or created from a single physical device or a small set of identical hardware configurations.
Abnormal Velocity: Rapid-fire account creations, logins, or promo redemptions that happen in tight clusters, often faster than humanly possible.
Shared Infrastructure: Different accounts frequently rotating through the same pools of residential proxies or VPNs to mask their origins.
Fraudsters are networking. Are businesses too?
Insights from Bureau and several industry forums highlight a dangerous asymmetry: while fraudsters are hyper-connected, the businesses defending against them remain largely siloed.
Fighting networked fraud requires a collaborative approach. It is, therefore, essential to understand why fraud rings are able to succeed despite growing investments in fraud prevention solutions. Two compelling reasons include:
1. The "visibility gap" in defense
Fraudsters exploit the fragmented visibility between different sectors as explained below:
Isolated Data Sets: A bank may see a transaction as "low risk" because the account balance is stable. However, a marketplace might see the same user linked to 10 failed KYC attempts earlier that day. Without sharing these signals, neither party sees the full picture.
The Silo Effect: Financial institutions often focus solely on transaction data, whereas online marketplaces focus on behavioral signals. Fraudsters hide in the white space between these two, moving funds from a compromised account to a mule bank account.
Repeatable Schemes: Because businesses don't communicate, a fraudster can use a successful tactic at Company A, and then move to Company B, C, and D using the exact same playbook before any industry-wide warning is triggered.
2. Barriers to collaboration
Despite the clear need for a network to fight a network, several hurdles prevent banks and platforms from working together:
Perceived Legal and Privacy Barriers: Many institutions fear that sharing specific fraud signals (like device IDs or PII) will violate data privacy laws like GDPR or DPDP. This legal paranoia often outweighs the drive to share threat intelligence.
Competitive Instincts: Some businesses view their fraud prevention data as a proprietary advantage rather than a collective necessity, leading to a culture where peers are seen as rivals rather than allies in security.
Lack of Standardization: Even when institutions want to share data, their systems often lack a common language. Risk scores and device fingerprints at a neobank may not be compatible with the legacy systems of a traditional bank.
3. The path forward: Collective intelligence
Fraud doesn't start, stay, or finish within a single institution. Bad actors spend their days actively probing vulnerabilities across multiple organizations. These patterns are invisible without cross-industry fraud intelligence. Therefore, the only way to dismantle networked fraud rings is through intelligence sharing and unified risk decisioning using:
Graph Identity Networks: To link digital footprints (emails, phone numbers, device IDs) across different platforms, enabling businesses to spot a fraud ring's pattern even if individual transactions look normal.
Shared Risk Signals: Moving from reactive (blocking a card after a theft) to proactive (flagging a device that has been seen in three different fraud rings across the industry) is only possible through shared intelligence.
Fraud data consortiums and graph identity networks, whether shared or private, are the way forward.
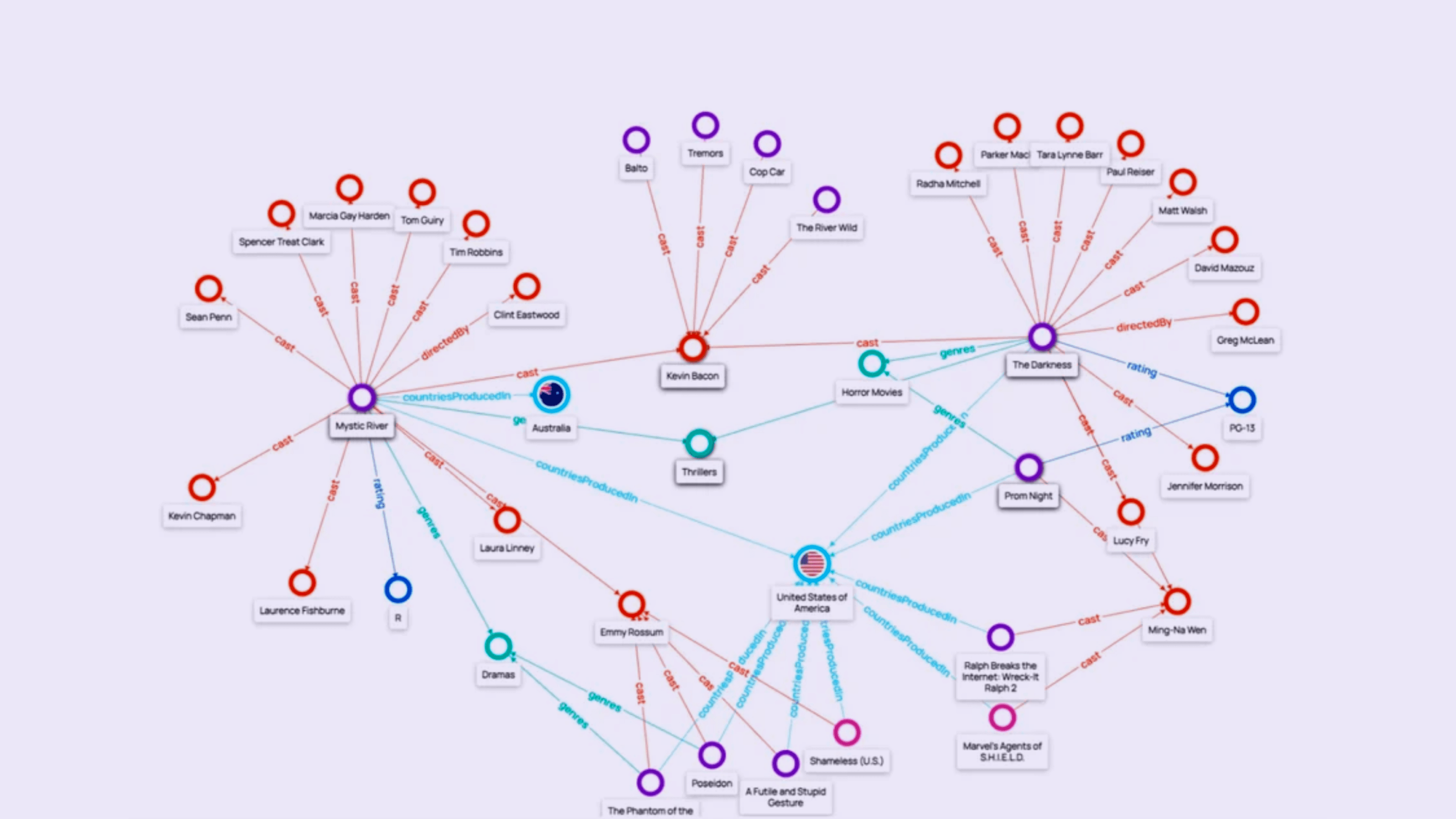
How Bureau leverages networked defenses
To combat the organized nature of modern fraud, Bureau employs a two-tiered, networked defense strategy that matches the scale and sophistication of fraud rings.
1. Foundational point solutions
These provide the first layer of defense by detecting specific, local indicators of fraud:
Device Intelligence: Identifies device farms and botnets, with 99.7% persistence, by analyzing hardware signatures, emulators, and high device-to-account ratios.
Behavioral Biometrics: Distinguishes humans from bots by analyzing interaction patterns (typing, scrolling, and more) to stop account takeovers and synthetic identity abuse.
2. Advanced networked defense (Graph Networks)
BureauID connects isolated events to expose entire fraud rings:
Bureau GIN (Graph Identity Network): Maps billions of identity attributes (emails, IPs, devices) as interconnected nodes to detect shared infrastructure and collusion loops in real-time.
Fraud Prevention Consortiums: Facilitates anonymous signal-sharing across organizations to instantly flag fraudsters moving between different platforms.
Private Graph Networks: Enables enterprises to map internal interactions to detect sophisticated promo abuse and internal collusion.
By combining targeted intelligence with collaborative graph networks, Bureau ensures that the defenses are as networked as the fraudsters themselves, such that online businesses can answer the challenge: Fraudsters are networking, are you? with a decisive "Yes." To learn more, talk to an expert now.
Globally, people and businesses are losing money to organized fraud rings and networks from account takeovers, promo abuse and chargeback fraud. The FBI and Internet Crime Complaint Center (IC3) have issued several public service announcements (such as this) regarding evolving cyber threats and financial crimes, especially during the holiday season, where people are prone to losing money to fraudsters, often a part of large scale criminal rings and networks.
The rising tide of scams has also led the FBI to launch the TakeABeat campaign - a public awareness initiative to ensure people remain safe from fraud.
Fraud is becoming increasingly sophisticated and networked. While device networks may be local or trans-national, fraudsters are leveraging criminal toolkits comprising AI, deepfakes, and generative AI to automate and scale fraud. These tools help criminals make fraud schemes more believable and allow smaller rings to operate like massive organizations.
Related Read: A Food Delivery Company Eliminates a 2,700+ User Fraud Ring
“Fraudsters are networking, Are businesses too?” This is not just a catchy line that has caught the attention of bankers, financial institutions, and online marketplaces alike, but indeed a hardhitting fact revealed by several investigations.

How fraudsters use networked infrastructure and tools
Fraudsters use centralized "farms" and automated networks to scale attacks that would be impossible for single individuals. These often include:
Device Farms: Collections of physical smartphones or virtual emulators that simulate thousands of "unique" users from a single location. These are used to bypass device-based limits for sign-up bonuses and referral rewards.
Botnets and Automated Scripts: Networks of hijacked or automated accounts that perform "credential stuffing" to take over accounts en masse. AI-driven bots are now increasingly being used to automate multi-stage attacks and simulate legitimate user engagement.
SIM Banks: Groups of devices used to bypass SMS-based two-factor authentication (2FA). They manage thousands of virtual or physical phone numbers for mass account verification.

Coordination among fraud rings
As has emerged from multiple investigations across markets, fraud today is a highly organized, professionalized "business" model. And fraudsters operate as coordinated syndicates that mimic legitimate corporate structures with:.
Specialized Roles: Much like a tech startup, fraud rings have "departmental" roles, some members focus on data harvesting (phishing), others on money laundering (mules), and some on technical evasion (spoofing devices).
Infrastructure Sharing: These networks share "fraud-as-a-service" toolkits, including jailbroken devices, proxy IPs, and virtual SIMs, allowing them to scale attacks rapidly across multiple platforms.
Cross-platform Probing: Rings often "poke" a system to find a vulnerability. Once a weakness is found in one bank or marketplace, the entire network is alerted to exploit the same gap across other institutions with similar profiles.
Related Read: What are Money Mules
The common modus operandi of a fraud ring includes:
Collusion Loops: Networks where "buyers" and "sellers" in marketplaces coordinate fake transactions to trigger referral payouts and sign-up credits.
Multi-stage Operations: Account takeover is often just the "entry point." Once a network gains access to legitimate accounts, they are used to farm loyalty points, distribute malware, or conduct larger financial transfers to "mule networks".
Identity Harvesting: Rings use stolen data from past breaches to create "synthetic identities", combinations of real and fake data, to bypass identity verification processes (KYC) at scale.
Indicators of networked activity
Security systems detect networked fraud by identifying clusters of behavior that lack typical human randomness. Some common telltales include:
Proximity-based Anomalies: Clusters of hundreds of "unique" devices operating from the same precise physical location; a hallmark of a physical device farm.
High Device-to-Account Ratios: Multiple accounts (often hundreds) being accessed or created from a single physical device or a small set of identical hardware configurations.
Abnormal Velocity: Rapid-fire account creations, logins, or promo redemptions that happen in tight clusters, often faster than humanly possible.
Shared Infrastructure: Different accounts frequently rotating through the same pools of residential proxies or VPNs to mask their origins.

Fraudsters are networking. Are businesses too?
Insights from Bureau and several industry forums highlight a dangerous asymmetry: while fraudsters are hyper-connected, the businesses defending against them remain largely siloed.
Fighting networked fraud requires a collaborative approach. It is, therefore, essential to understand why fraud rings are able to succeed despite growing investments in fraud prevention solutions. Two compelling reasons include:
1. The "visibility gap" in defense
Fraudsters exploit the fragmented visibility between different sectors as explained below:
Isolated Data Sets: A bank may see a transaction as "low risk" because the account balance is stable. However, a marketplace might see the same user linked to 10 failed KYC attempts earlier that day. Without sharing these signals, neither party sees the full picture.
The Silo Effect: Financial institutions often focus solely on transaction data, whereas online marketplaces focus on behavioral signals. Fraudsters hide in the white space between these two, moving funds from a compromised account to a mule bank account.
Repeatable Schemes: Because businesses don't communicate, a fraudster can use a successful tactic at Company A, and then move to Company B, C, and D using the exact same playbook before any industry-wide warning is triggered.
2. Barriers to collaboration
Despite the clear need for a network to fight a network, several hurdles prevent banks and platforms from working together:
Perceived Legal and Privacy Barriers: Many institutions fear that sharing specific fraud signals (like device IDs or PII) will violate data privacy laws like GDPR or DPDP. This legal paranoia often outweighs the drive to share threat intelligence.
Competitive Instincts: Some businesses view their fraud prevention data as a proprietary advantage rather than a collective necessity, leading to a culture where peers are seen as rivals rather than allies in security.
Lack of Standardization: Even when institutions want to share data, their systems often lack a common language. Risk scores and device fingerprints at a neobank may not be compatible with the legacy systems of a traditional bank.
3. The path forward: Collective intelligence
Fraud doesn't start, stay, or finish within a single institution. Bad actors spend their days actively probing vulnerabilities across multiple organizations. These patterns are invisible without cross-industry fraud intelligence. Therefore, the only way to dismantle networked fraud rings is through intelligence sharing and unified risk decisioning using:
Graph Identity Networks: To link digital footprints (emails, phone numbers, device IDs) across different platforms, enabling businesses to spot a fraud ring's pattern even if individual transactions look normal.
Shared Risk Signals: Moving from reactive (blocking a card after a theft) to proactive (flagging a device that has been seen in three different fraud rings across the industry) is only possible through shared intelligence.
Fraud data consortiums and graph identity networks, whether shared or private, are the way forward.

How Bureau leverages networked defenses
To combat the organized nature of modern fraud, Bureau employs a two-tiered, networked defense strategy that matches the scale and sophistication of fraud rings.
1. Foundational point solutions
These provide the first layer of defense by detecting specific, local indicators of fraud:
Device Intelligence: Identifies device farms and botnets, with 99.7% persistence, by analyzing hardware signatures, emulators, and high device-to-account ratios.
Behavioral Biometrics: Distinguishes humans from bots by analyzing interaction patterns (typing, scrolling, and more) to stop account takeovers and synthetic identity abuse.
2. Advanced networked defense (Graph Networks)
BureauID connects isolated events to expose entire fraud rings:
Bureau GIN (Graph Identity Network): Maps billions of identity attributes (emails, IPs, devices) as interconnected nodes to detect shared infrastructure and collusion loops in real-time.
Fraud Prevention Consortiums: Facilitates anonymous signal-sharing across organizations to instantly flag fraudsters moving between different platforms.
Private Graph Networks: Enables enterprises to map internal interactions to detect sophisticated promo abuse and internal collusion.
By combining targeted intelligence with collaborative graph networks, Bureau ensures that the defenses are as networked as the fraudsters themselves, such that online businesses can answer the challenge: Fraudsters are networking, are you? with a decisive "Yes." To learn more, talk to an expert now.
TABLE OF CONTENTS
See More
TABLE OF CONTENTS
See More
Recommended Blogs

Building Real-time Defenses in an Always-on Economy
In an always-on, connected economy, risks are created in real-time, rather than at discrete checkpoints. Defense strategies must, accordingly, level up to measure trust throughout the entire user experience, from first interaction to every single transaction. This always-on protection needs connected signals, adaptive decisioning, and protection that can keep pace with evolving digital behaviors and access methods.

iGaming KYC: Balancing Risk, Compliance, and Player Experience
KYC-driven identity verification is a core element for fraud prevention in iGaming. It helps these platforms establish trust at onboarding by creating a secure, fair, and sustainable ecosystem, preventing abuse, preserving integrity of the platform, and ensuring regulatory compliance.

How Device Intelligence Adapts to Global Data Sovereignty
Global data sovereignty laws are forcing financial institutions to rethink device intelligence, redesign fraud architecture, and operate compliant, real-time risk systems across increasingly fragmented regulatory environments. What this means in practice is a fundamental shift in how businesses design, deploy, and govern fraud systems across regions.
TABLE OF CONTENTS
See Less
TABLE OF CONTENTS
See Less



Solutions
Resources
© 2026 Bureau . All rights reserved.
Solutions
Solutions
Industries
Industries
Resources
Resources
Company
Company
Solutions
Solutions
Industries
Industries
Resources
Resources
Company
Company
© 2025 Bureau . All rights reserved. Privacy Policy. Terms of Service.
© 2025 Bureau . All rights reserved.
Privacy Policy. Terms of Service.
Follow Us
Leave behind fragmented tools. Stop fraud rings, cut false declines, and deliver secure digital journeys at scale
Our Presence
















Leave behind fragmented tools. Stop fraud rings, cut false declines, and deliver secure digital journeys at scale
Our Presence

















