Jan 23, 2026
Global KYC and AML Regulations: Part 1 - What Regulators Really Expect
Global KYC and AML Regulations: Part 1 - What Regulators Really Expect
Global KYC and AML Regulations: Part 1 - What Regulators Really Expect
Despite local differences in KYC and AML rules, global regulatory expectations are aligning at remarkable speed. Across regions, supervisors are converging on the same outcomes: risk-led controls, continuous oversight, and decisions that can be clearly explained and audited. These evolving expectations are reshaping how institutions must approach compliance.
Author
Team Bureau



TABLE OF CONTENTS
See Less
This two-part series explores how global KYC and AML regulation is evolving and what that evolution actually means for financial institutions on the ground. Part 1, this blog post, focuses on regulatory direction. It discusses supervisors' expectations, how they evaluate compliance, and why many traditional approaches quietly fall short.
For decades, KYC and AML compliance followed a familiar pattern. Institutions collected documents, ran checks before onboarding, applied preset rules, and documented evidence that procedures were followed. If all the boxes were ticked, compliance was assumed.
That tested model is no longer feasible.
Across major global jurisdictions, regulators are moving away from checklist-driven compliance and toward outcome-based expectations. They are far less interested in how many controls exist on paper and are becoming more focused on whether those controls actually aid in curbing financial crime.
It is not a seismic shift, but a subtle one. Regulators are not vocally saying, “run fewer checks.” Instead they are asking, “show how the controls work.”
Related Read: The Ultimate KYC and AML Checklist for BFSI Compliance Teams
What regulators are converging on, globally
While KYC and AML regulations continue to vary by jurisdiction, global regulatory direction is converging at an accelerated pace than most institutions can imagine. Irrespective of whether the regulator is located in North America, Europe, APAC, or the Middle East, the underlying regulatory expectations increasingly direct towards the same capabilities.
Regulators are implicitly pushing institutions toward:
Risk-based controls
Continuous monitoring
Explainability and auditability
Risk-based controls
Today, institutions are expected to think beyond paper-based controls and understand where the risk actually lives. They are expected to think and apply contextually relevant controls that can arrest risk before it spreads. This means deeper scrutiny for high-risk behaviors and transactions, and less friction for low-risk activity.

Continuous monitoring
In the past, checks and balances were considered completed at the onboarding stage. Regulators expect institutions to detect emerging risk over time: when behavior changes, when devices change, when networks form, or when activity patterns drift.
This expectation applies equally to fraud, AML, and KYC. The lines between these domains are, therefore, blurring; and regulators are increasingly comfortable with that reality.
Related Webinar: Rethinking Onboarding - 5 Ways to Turn Onboarding Into a Growth Engine
Explainability and auditability
Although controls are becoming outcome-driven, regulators are not backing away from accountability. If anything, they are raising the bar.
Institutions must be able to answer basic but difficult questions such as:
Why was this customer approved?
Why was this transaction allowed?
Why was this refund authorized?
Why was this account blocked or not blocked?
Importantly, regulators do not mandate specific tools, vendors, or models. They mandate capabilities.
How those capabilities are implemented is left to the institution, but the outcomes are not negotiable.
What regulators actually evaluate during reviews
There is a common perception that the primary focus of any audit is documentation and process adherence. However, modern regulatory reviews go farther to ensure whether these controls help in risk management. Supervisors increasingly evaluate institutions across three dimensions that go beyond formal compliance artifacts.
Intent
Effectiveness
Auditability

Intent
Regulators assess whether controls were designed to genuinely reduce risk or whether they satisfy minimum requirements.
Effectiveness
This is the moment of truth where the controls are stress tested for measurable impact. They try to answer questions like:
Are fraud losses declining?
Is mule activity being disrupted earlier?
Are account takeovers being detected before damage occurs?
Auditability
Every major decision must have an audit trail. Decisions taken a long time ago should be possible to reverse engineer. This includes the signals used, the logic applied, and the rationale behind outcomes.
Black-box decisions without clear audit trails increasingly attract scrutiny.
The key insight, therefore, is that compliance theater may pass surface-level reviews, but it fails deeper examinations. Well-governed, intelligence-driven controls mitigate risk far better under regulatory pressure.
Why this creates a technology gap for many institutions
The regulatory shift exposes a growing mismatch between modern risk expectations and legacy compliance infrastructure.
Most traditional KYC programs remain document-centric. They rely heavily on static identity attributes collected at onboarding and updated infrequently.
Related Read: Navigating the Complex World of KYC
Related Read: Navigating the Complex World of KYC |
Additionally, most traditional AML programs still depend on rules and thresholds. These rules and thresholds are often tuned or revisited over a period of time to reduce false positives, rather than with the motive of improving detection.
Meanwhile, modern fraud and financial crime operate differently. They are:
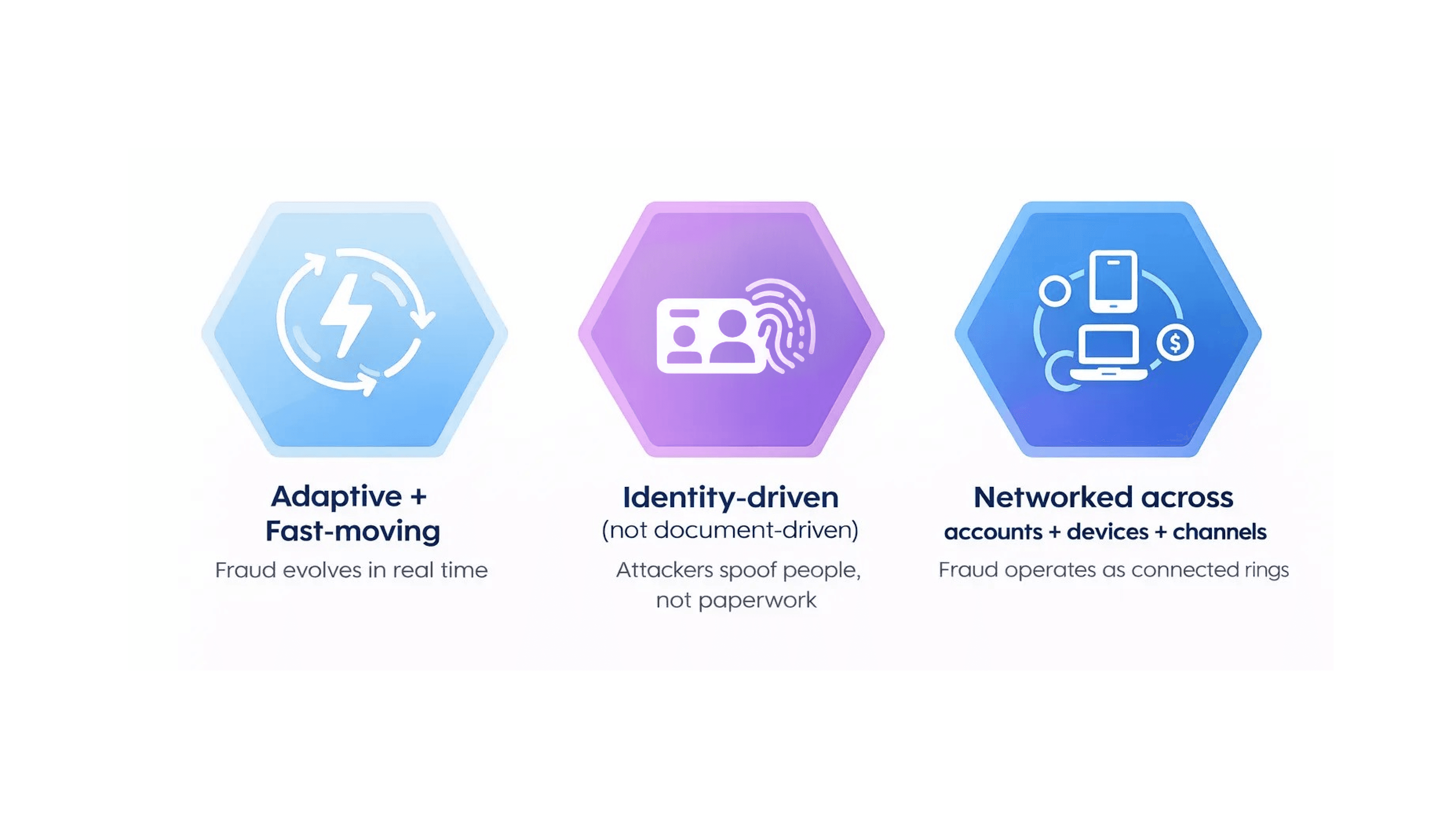
The result is a widening gap.
Many institutions technically comply with regulatory requirements while missing emerging risk entirely. They satisfy regulatory compliances on paper but fail to capture its spirit of risk minimization or avoidance entirely.
This gap is not just an operational problem. It is a regulatory risk in its own right. Learn how Bureau can help plug in this gap, talk to an expert now.
Key takeaways
Minimizing risk and improving compliance is a priority for regulators. They have a mandate for outcomes and are not particular about the tools used to achieve the same.
Institutions that rely on traditional checklist-based checks instead of deep intelligence may appear compliant on the surface. However, even without their knowledge they could be carrying hidden regulatory exposure beneath the shallow controls.
The future of KYC and AML compliance belongs to institutions that understand this distinction and act on it.
The real question is no longer what regulation says. It is how institutions should respond.
Part 2 of this series will explore what effective execution looks like in practice. Also, how unified risk decisioning enables institutions to meet regulatory expectations without sacrificing speed, customer experience, or control. Watch this space.
This two-part series explores how global KYC and AML regulation is evolving and what that evolution actually means for financial institutions on the ground. Part 1, this blog post, focuses on regulatory direction. It discusses supervisors' expectations, how they evaluate compliance, and why many traditional approaches quietly fall short.
For decades, KYC and AML compliance followed a familiar pattern. Institutions collected documents, ran checks before onboarding, applied preset rules, and documented evidence that procedures were followed. If all the boxes were ticked, compliance was assumed.
That tested model is no longer feasible.
Across major global jurisdictions, regulators are moving away from checklist-driven compliance and toward outcome-based expectations. They are far less interested in how many controls exist on paper and are becoming more focused on whether those controls actually aid in curbing financial crime.
It is not a seismic shift, but a subtle one. Regulators are not vocally saying, “run fewer checks.” Instead they are asking, “show how the controls work.”
Related Read: The Ultimate KYC and AML Checklist for BFSI Compliance Teams
What regulators are converging on, globally
While KYC and AML regulations continue to vary by jurisdiction, global regulatory direction is converging at an accelerated pace than most institutions can imagine. Irrespective of whether the regulator is located in North America, Europe, APAC, or the Middle East, the underlying regulatory expectations increasingly direct towards the same capabilities.
Regulators are implicitly pushing institutions toward:
Risk-based controls
Continuous monitoring
Explainability and auditability
Risk-based controls
Today, institutions are expected to think beyond paper-based controls and understand where the risk actually lives. They are expected to think and apply contextually relevant controls that can arrest risk before it spreads. This means deeper scrutiny for high-risk behaviors and transactions, and less friction for low-risk activity.

Continuous monitoring
In the past, checks and balances were considered completed at the onboarding stage. Regulators expect institutions to detect emerging risk over time: when behavior changes, when devices change, when networks form, or when activity patterns drift.
This expectation applies equally to fraud, AML, and KYC. The lines between these domains are, therefore, blurring; and regulators are increasingly comfortable with that reality.
Related Webinar: Rethinking Onboarding - 5 Ways to Turn Onboarding Into a Growth Engine
Explainability and auditability
Although controls are becoming outcome-driven, regulators are not backing away from accountability. If anything, they are raising the bar.
Institutions must be able to answer basic but difficult questions such as:
Why was this customer approved?
Why was this transaction allowed?
Why was this refund authorized?
Why was this account blocked or not blocked?
Importantly, regulators do not mandate specific tools, vendors, or models. They mandate capabilities.
How those capabilities are implemented is left to the institution, but the outcomes are not negotiable.
What regulators actually evaluate during reviews
There is a common perception that the primary focus of any audit is documentation and process adherence. However, modern regulatory reviews go farther to ensure whether these controls help in risk management. Supervisors increasingly evaluate institutions across three dimensions that go beyond formal compliance artifacts.
Intent
Effectiveness
Auditability

Intent
Regulators assess whether controls were designed to genuinely reduce risk or whether they satisfy minimum requirements.
Effectiveness
This is the moment of truth where the controls are stress tested for measurable impact. They try to answer questions like:
Are fraud losses declining?
Is mule activity being disrupted earlier?
Are account takeovers being detected before damage occurs?
Auditability
Every major decision must have an audit trail. Decisions taken a long time ago should be possible to reverse engineer. This includes the signals used, the logic applied, and the rationale behind outcomes.
Black-box decisions without clear audit trails increasingly attract scrutiny.
The key insight, therefore, is that compliance theater may pass surface-level reviews, but it fails deeper examinations. Well-governed, intelligence-driven controls mitigate risk far better under regulatory pressure.
Why this creates a technology gap for many institutions
The regulatory shift exposes a growing mismatch between modern risk expectations and legacy compliance infrastructure.
Most traditional KYC programs remain document-centric. They rely heavily on static identity attributes collected at onboarding and updated infrequently.
Related Read: Navigating the Complex World of KYC
Related Read: Navigating the Complex World of KYC |
Additionally, most traditional AML programs still depend on rules and thresholds. These rules and thresholds are often tuned or revisited over a period of time to reduce false positives, rather than with the motive of improving detection.
Meanwhile, modern fraud and financial crime operate differently. They are:

The result is a widening gap.
Many institutions technically comply with regulatory requirements while missing emerging risk entirely. They satisfy regulatory compliances on paper but fail to capture its spirit of risk minimization or avoidance entirely.
This gap is not just an operational problem. It is a regulatory risk in its own right. Learn how Bureau can help plug in this gap, talk to an expert now.
Key takeaways
Minimizing risk and improving compliance is a priority for regulators. They have a mandate for outcomes and are not particular about the tools used to achieve the same.
Institutions that rely on traditional checklist-based checks instead of deep intelligence may appear compliant on the surface. However, even without their knowledge they could be carrying hidden regulatory exposure beneath the shallow controls.
The future of KYC and AML compliance belongs to institutions that understand this distinction and act on it.
The real question is no longer what regulation says. It is how institutions should respond.
Part 2 of this series will explore what effective execution looks like in practice. Also, how unified risk decisioning enables institutions to meet regulatory expectations without sacrificing speed, customer experience, or control. Watch this space.
TABLE OF CONTENTS
See More
Recommended Blogs

How Middle East Banks Can Rethink Fraud Prevention
Rapid digital adoption is reshaping banking across the Middle East. Instant onboarding, digital wallets, and super apps are now the norm, expanding the attack surface in the process. To deliver strong protection without adding friction, banks in the region must counter AI-driven fraud with connected intelligence across identity, devices, and behavior.

Building Real-time Defenses in an Always-on Economy
In an always-on, connected economy, risks are created in real-time, rather than at discrete checkpoints. Defense strategies must, accordingly, level up to measure trust throughout the entire user experience, from first interaction to every single transaction. This always-on protection needs connected signals, adaptive decisioning, and protection that can keep pace with evolving digital behaviors and access methods.

iGaming KYC: Balancing Risk, Compliance, and Player Experience
KYC-driven identity verification is a core element for fraud prevention in iGaming. It helps these platforms establish trust at onboarding by creating a secure, fair, and sustainable ecosystem, preventing abuse, preserving integrity of the platform, and ensuring regulatory compliance.
TABLE OF CONTENTS
See Less


Solutions
Resources
© 2026 Bureau . All rights reserved.
Solutions
Industries
Resources
Company
Solutions
Industries
Resources
Company
© 2026 Bureau . All rights reserved.
Follow Us
Leave behind fragmented tools. Stop fraud rings, cut false declines, and deliver secure digital journeys at scale
Our Presence












Leave behind fragmented tools. Stop fraud rings, cut false declines, and deliver secure digital journeys at scale
Our Presence












© 2026 Bureau . All rights reserved.

