Dec 26, 2025
From In-House Tools to Unified Fraud Intelligence
From In-House Tools to Unified Fraud Intelligence
From In-House Tools to Unified Fraud Intelligence
Device fingerprinting helps identify spoofing, bots, and repeat abuse by recognizing unique device attributes, even when fraudsters spoof emails or IPs. For businesses, the decision, whether to build this capability in-house or rely on a specialized partner, can directly shape how quickly teams can adapt to evolving threats.
Author
Team Bureau



TABLE OF CONTENTS
See Less
Sophisticated fraud schemes powered by artificial intelligence and automation continue to surge and help fraudsters target gaps in traditional controls. It is estimated that generative AI may power losses worth $40 billion by 2027.
At the same time, businesses are under pressure to streamline their onboarding and transaction flows to deliver frictionless user experiences. This rush creates blind spots and vulnerabilities that can be easily exploited by automated systems.
Solutions like device fingerprinting offer a reliable method of identifying the unique attributes of a device to detect spoofing, bots, and repeated abuse. When done well, device fingerprinting can act as a strong shield against fraud even when user identifiers like email or IP addresses are changed.
However, this creates a dilemma for leaders: should they build device fingerprinting capabilities internally, or buy them from a specialized partner?
This decision has a long-term effect as it would decide how quickly IT teams can respond to evolving threats.
Device Fingerprinting: Decoding A Core Fraud Signal
Think of a device fingerprint as a digital DNA that links machines and sessions across time and context. This link helps fraud teams diagnose patterns in user behavior that can lead to fraud discovery.
Device fingerprinting provides the much-needed capabilities to improve resilience and prevent frauds proactively.
Below are key ways device fingerprinting strengthens fraud detection:
Device spoofing action
Fraudsters often alter device signals using emulators, virtual machines, or masking tools, to bypass security mechanisms. Device fingerprinting looks deep beneath the surface-level identifiers to spot traits that determine if it is a spoofed device.
Fraud ring identification
Fraud rings use the same devices to create multiple accounts, test stolen accounts, or automate attacks. Device fingerprinting makes it possible to identify the devices individually and prevent fraud from advancing.
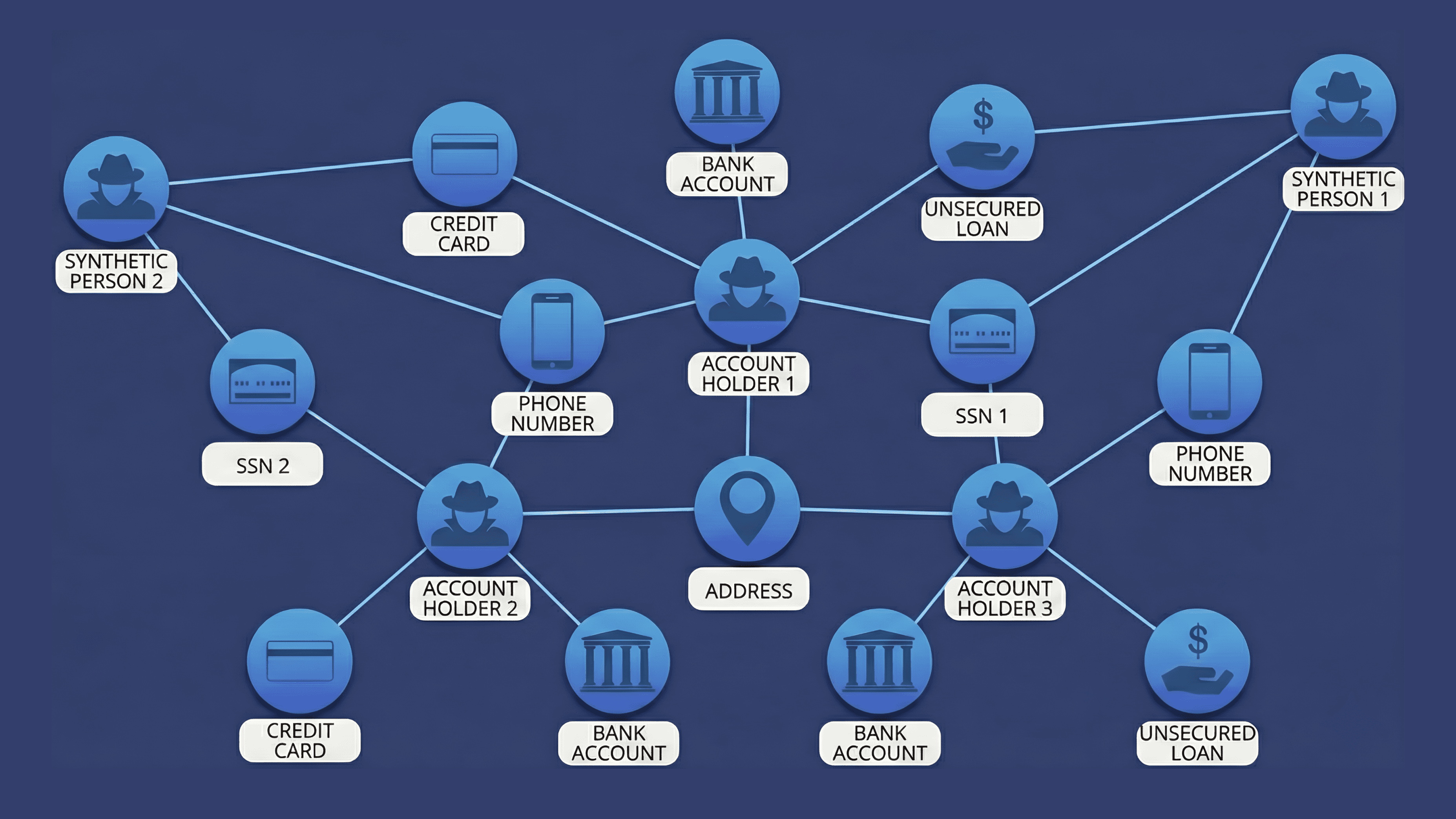
Account takeover prevention (ATO)
Device fingerprints reveal whether an access request is from a genuine or high-risk device to flag the device for further verification. This helps stop account takeover early in its tracks, before damage can happen.
Synthetic identity detection
A synthetic identity is created by blending real and fake identity attributes. In a quick glance, synthetic identities look legit, but are actually controlled by fraudsters. Device fingerprinting helps spot patterns in reuse of the same devices or exhibit abnormal device behavior.
The Many Challenges in Building Device Fingerprinting
Building device fingerprinting in-house looks straightforward at first. In practice, however, it is one of the hardest fraud signals to get right due to several challenges described below:
High engineering costs to build frontend, backend, data engineering, and security teams.
The opportunity cost factor. Every effort spent on maintaining fingerprint logic could be time better spent on revenue maximization, CX enhancement, or strengthening core platform capabilities.
Growing technical debt. Device fingerprinting systems can become obsolete quickly. Even the slightest change in browsers or operating systems could jeopardize fingerprint traits and their trackability.
Need for deep fraud expertise. Device fingerprinting is a continuous loop of upgrading research and expertise. It needs deep fraud expertise and often internal teams cannot exert the time or effort required for such fraud analysis
Even if these inherent challenges of building device fingerprinting are taken care of, there is still the challenge of maintaining it and ensuring compliance.
The Maintenance and Compliance Trap
The hardest part of device fingerprinting is not the initial build. It is everything that follows.
Constant maintenance
Browsers and operating systems are bound to be updated from time to time that can weaken fingerprint accuracy.
Platform-driven disruption
Privacy changes from major device makers like Apple, Google, and browser vendors can limit access to device signals. Currently, initiatives like App Tracking Transparency, Android privacy controls can significantly affect device signal reliability.
Enablement and training costs
Investigators need training to interpret device risk signals, resolve edge cases, and avoid bias. As teams scale or change, these costs can inflate.
Privacy and compliance risk
Device identifiers may face scrutiny under data protection laws, such as the GDPR. Organizations are required to manage consent, retention, and auditability thoroughly. Even the smallest gaps can result in non-compliance, adding to the fraud losses.
These issues compound when device fingerprinting feeds into wider fraud and AML workflows. Errors can propagate into investigations, reporting, and audits. What begins as a technical challenge can quickly become an enterprise risk and compliance burden.
Time-to-Market Vs. Time-to-Value
Time is one of the most underestimated risks in building in-house fraud systems and programs.
Long MVP timelines
A typical device fingerprinting initiative ranges from planning to implementation; and can take anywhere from six months to one year. Unfortunately, during this period, the initial data fraud signals and patterns gathered may evolve or become obsolete, making fraud defenses less effective.
Fraud losses during the build phase
Fraudsters do not stop attacking when fraud systems are under development. The gaps in fraud detection during the long build cycles can result in losses, customer experience mishaps, and even prove detrimental to security posture.
Extended testing and tuning cycles
Assuming the device fingerprinting system is launched in a steadfast manner, it will still need months of continuous training and development to filter false positives. In the meantime, fraud investigators will have to rely on manual checks, which slows down responses and inflates operational costs.
Faster go-live with specialized partners
Pre-built solutions shorten time-to-market by starting with proven signal coverage and risk models. This accelerates time-to-value, not just deployment. Organizations can begin reducing fraud risk sooner, while iterating safely on top of a stable foundation.
The core risk is not the delay in implementation, but the operational exposure during the delay. For many organizations, that risk can outweigh the perceived benefits of full in-house control.
The Data and Case Management Problem
When device fingerprinting data flows into investigations, weaknesses in data handling and case management become visible fast.
Problem area | What breaks in practice |
|---|---|
Data visualization | Raw device data is hard to interpret without clear visual context. Investigators struggle to spot patterns across sessions, accounts, and devices. |
Investigator usability | Complex interfaces slow reviews. Analysts spend time navigating tools instead of making decisions. |
Dashboard and analytics limits | Internal dashboards often lack flexible views, trend analysis, or cross-case comparisons needed for fraud detection. |
Fragmented case views | Device data, transaction alerts, and identity signals live in separate tools, creating incomplete investigations. |
Manual alert stitching | Analysts must connect alerts across systems by hand, which increases errors and review time. |
Investigation inefficiency | Slow reviews lead to delayed action, higher costs, and missed fraud patterns. |
Build Vs. Buy: The Familiar Deadlock
The build vs. buy deadlock is not a new introduction. Business leaders have wrestled with it for a long time. It becomes evident every time a new technology, platform, or a workflow has to be adopted. Device fingerprinting is one of the latest introductions in the fraud infrastructure dilemma.
While building promises total control, buying provides speed and instant availability.
However, both approaches come with trade-offs that are sometimes not fully understood or even underestimated.
Engineering enthusiasm vs. operational reality
Engineering teams are bound to favor building, since it sets the stage to build a clean, customized, technically aligned system that is easier to build upon. Their initial prototypes and test builds might also work flawlessly.
In the real-world fraud scenarios that continuously evolve and upgrade, a homegrown build could become a technical burden with a heavy cost.
Cost vs. control tension
Buying relieves the pressure of development timelines and maintenance costs. However, it can make the business dependent on the external vendor.
Why the deadlock persists
It is not easy for fraud leaders to choose between two imperfect options. Build too much, and teams drown in maintenance. Buy too much, and systems become rigid. That said, there is a third option.
The Third Option: Buy the Foundation, Build the Differentiation
Build or buy are often treated as the only two alternatives available. However, there is also the third hybrid option that can be more feasible and practical for organizations.
Buy the battle-tested foundation
Buying proven infrastructure reduces operational risk and accelerates time-to-value. Such infrastructure includes device fingerprinting, data ingestion, compliance controls, etc.
Build what makes fraud response unique
Risk thresholds, decision logic, workflows, and policy rules vary by industry and business model. Building on top of a battle-tested foundation allows teams to tailor fraud responses without taking up the heavy burden of maintenance.
Avoid rebuilding non-differentiating layers
Recreating plumbing rarely creates advantage. Most organizations do not win on how they collect device signals. They win on how they apply them. The Build + Buy model preserves control where it matters, while removing drag where it does not.
Ways to Keep Pace With Evolving Fraud
Fraud is a moving target. Fraudsters change their tactics as soon as existing vulnerabilities are closed and new defenses are raised. Organizations can keep pace with evolving fraud schemes and ensure that their user data is protected with these tactics:
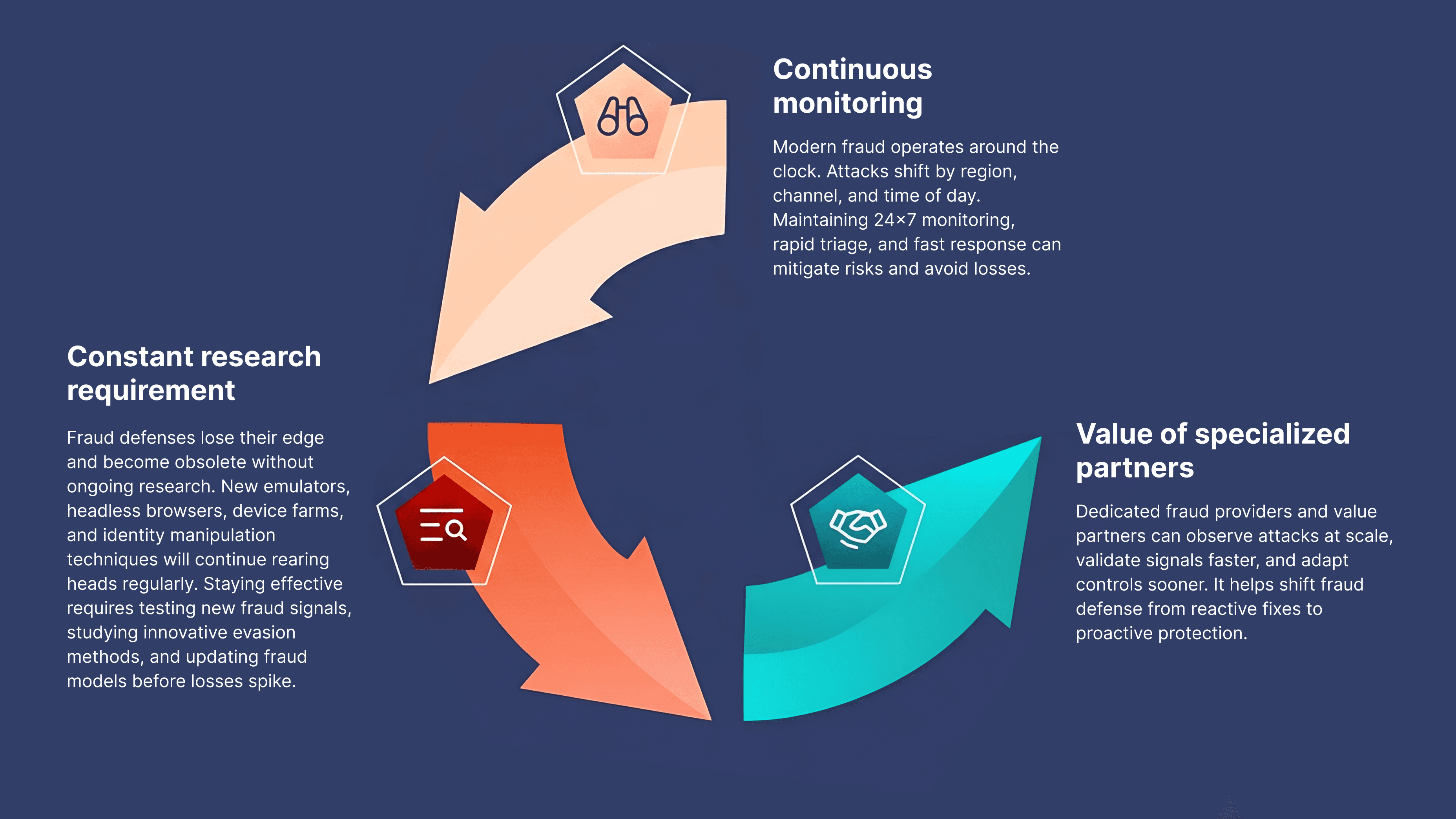
Skip the Burden, Focus on Outcomes
The build vs. buy debate no longer fits the reality of modern fraud prevention. Fraud systems must adapt fast, scale reliably, and meet growing compliance demands. That requires more than full ownership or outsourcing. Furthermore, the cost of fraud infrastructure is not limited to licenses or engineering hours. It includes opportunity cost, inherent risks, and fragmented efforts.
A better approach is to skip the burden and focus on fraud prevention outcomes. With Bureau businesses can reduce fraud losses, limit customer friction, and support investigators with clear, timely signals across the customer lifecycle.
Bureau’s Device ID delivers best-in-class fingerprinting with 99.7% device persistence in linking accounts and devices that helps reduce collusion-based abuse by over 95%. Powered by Bureau’s AI-driven Unified Risk Decisioning Platform, businesses can activate adaptive fraud responses from day one, while remaining compliant across regions. Bureau evaluates 200+ behavioral attributes and maps relationships across devices, accounts, and behaviors, to help modern businesses identify fraud rings and anomalies even when devices, credentials, or IPs appear clean.
Rethink device intelligence and fraud signals with Bureau to enable unified fraud decisioning across the customer lifecycle. Schedule a demo.
Sophisticated fraud schemes powered by artificial intelligence and automation continue to surge and help fraudsters target gaps in traditional controls. It is estimated that generative AI may power losses worth $40 billion by 2027.
At the same time, businesses are under pressure to streamline their onboarding and transaction flows to deliver frictionless user experiences. This rush creates blind spots and vulnerabilities that can be easily exploited by automated systems.
Solutions like device fingerprinting offer a reliable method of identifying the unique attributes of a device to detect spoofing, bots, and repeated abuse. When done well, device fingerprinting can act as a strong shield against fraud even when user identifiers like email or IP addresses are changed.

However, this creates a dilemma for leaders: should they build device fingerprinting capabilities internally, or buy them from a specialized partner?
This decision has a long-term effect as it would decide how quickly IT teams can respond to evolving threats.
Device Fingerprinting: Decoding A Core Fraud Signal
Think of a device fingerprint as a digital DNA that links machines and sessions across time and context. This link helps fraud teams diagnose patterns in user behavior that can lead to fraud discovery.
Device fingerprinting provides the much-needed capabilities to improve resilience and prevent frauds proactively.
Below are key ways device fingerprinting strengthens fraud detection:
Device spoofing action
Fraudsters often alter device signals using emulators, virtual machines, or masking tools, to bypass security mechanisms. Device fingerprinting looks deep beneath the surface-level identifiers to spot traits that determine if it is a spoofed device.
Fraud ring identification
Fraud rings use the same devices to create multiple accounts, test stolen accounts, or automate attacks. Device fingerprinting makes it possible to identify the devices individually and prevent fraud from advancing.

Account takeover prevention (ATO)
Device fingerprints reveal whether an access request is from a genuine or high-risk device to flag the device for further verification. This helps stop account takeover early in its tracks, before damage can happen.
Synthetic identity detection
A synthetic identity is created by blending real and fake identity attributes. In a quick glance, synthetic identities look legit, but are actually controlled by fraudsters. Device fingerprinting helps spot patterns in reuse of the same devices or exhibit abnormal device behavior.
The Many Challenges in Building Device Fingerprinting
Building device fingerprinting in-house looks straightforward at first. In practice, however, it is one of the hardest fraud signals to get right due to several challenges described below:
High engineering costs to build frontend, backend, data engineering, and security teams.
The opportunity cost factor. Every effort spent on maintaining fingerprint logic could be time better spent on revenue maximization, CX enhancement, or strengthening core platform capabilities.
Growing technical debt. Device fingerprinting systems can become obsolete quickly. Even the slightest change in browsers or operating systems could jeopardize fingerprint traits and their trackability.
Need for deep fraud expertise. Device fingerprinting is a continuous loop of upgrading research and expertise. It needs deep fraud expertise and often internal teams cannot exert the time or effort required for such fraud analysis
Even if these inherent challenges of building device fingerprinting are taken care of, there is still the challenge of maintaining it and ensuring compliance.
The Maintenance and Compliance Trap
The hardest part of device fingerprinting is not the initial build. It is everything that follows.
Constant maintenance
Browsers and operating systems are bound to be updated from time to time that can weaken fingerprint accuracy.
Platform-driven disruption
Privacy changes from major device makers like Apple, Google, and browser vendors can limit access to device signals. Currently, initiatives like App Tracking Transparency, Android privacy controls can significantly affect device signal reliability.
Enablement and training costs
Investigators need training to interpret device risk signals, resolve edge cases, and avoid bias. As teams scale or change, these costs can inflate.
Privacy and compliance risk
Device identifiers may face scrutiny under data protection laws, such as the GDPR. Organizations are required to manage consent, retention, and auditability thoroughly. Even the smallest gaps can result in non-compliance, adding to the fraud losses.
These issues compound when device fingerprinting feeds into wider fraud and AML workflows. Errors can propagate into investigations, reporting, and audits. What begins as a technical challenge can quickly become an enterprise risk and compliance burden.
Time-to-Market Vs. Time-to-Value
Time is one of the most underestimated risks in building in-house fraud systems and programs.
Long MVP timelines
A typical device fingerprinting initiative ranges from planning to implementation; and can take anywhere from six months to one year. Unfortunately, during this period, the initial data fraud signals and patterns gathered may evolve or become obsolete, making fraud defenses less effective.
Fraud losses during the build phase
Fraudsters do not stop attacking when fraud systems are under development. The gaps in fraud detection during the long build cycles can result in losses, customer experience mishaps, and even prove detrimental to security posture.
Extended testing and tuning cycles
Assuming the device fingerprinting system is launched in a steadfast manner, it will still need months of continuous training and development to filter false positives. In the meantime, fraud investigators will have to rely on manual checks, which slows down responses and inflates operational costs.
Faster go-live with specialized partners
Pre-built solutions shorten time-to-market by starting with proven signal coverage and risk models. This accelerates time-to-value, not just deployment. Organizations can begin reducing fraud risk sooner, while iterating safely on top of a stable foundation.
The core risk is not the delay in implementation, but the operational exposure during the delay. For many organizations, that risk can outweigh the perceived benefits of full in-house control.
The Data and Case Management Problem
When device fingerprinting data flows into investigations, weaknesses in data handling and case management become visible fast.
Problem area | What breaks in practice |
|---|---|
Data visualization | Raw device data is hard to interpret without clear visual context. Investigators struggle to spot patterns across sessions, accounts, and devices. |
Investigator usability | Complex interfaces slow reviews. Analysts spend time navigating tools instead of making decisions. |
Dashboard and analytics limits | Internal dashboards often lack flexible views, trend analysis, or cross-case comparisons needed for fraud detection. |
Fragmented case views | Device data, transaction alerts, and identity signals live in separate tools, creating incomplete investigations. |
Manual alert stitching | Analysts must connect alerts across systems by hand, which increases errors and review time. |
Investigation inefficiency | Slow reviews lead to delayed action, higher costs, and missed fraud patterns. |
Build Vs. Buy: The Familiar Deadlock
The build vs. buy deadlock is not a new introduction. Business leaders have wrestled with it for a long time. It becomes evident every time a new technology, platform, or a workflow has to be adopted. Device fingerprinting is one of the latest introductions in the fraud infrastructure dilemma.
While building promises total control, buying provides speed and instant availability.
However, both approaches come with trade-offs that are sometimes not fully understood or even underestimated.
Engineering enthusiasm vs. operational reality
Engineering teams are bound to favor building, since it sets the stage to build a clean, customized, technically aligned system that is easier to build upon. Their initial prototypes and test builds might also work flawlessly.
In the real-world fraud scenarios that continuously evolve and upgrade, a homegrown build could become a technical burden with a heavy cost.
Cost vs. control tension
Buying relieves the pressure of development timelines and maintenance costs. However, it can make the business dependent on the external vendor.
Why the deadlock persists
It is not easy for fraud leaders to choose between two imperfect options. Build too much, and teams drown in maintenance. Buy too much, and systems become rigid. That said, there is a third option.
The Third Option: Buy the Foundation, Build the Differentiation
Build or buy are often treated as the only two alternatives available. However, there is also the third hybrid option that can be more feasible and practical for organizations.
Buy the battle-tested foundation
Buying proven infrastructure reduces operational risk and accelerates time-to-value. Such infrastructure includes device fingerprinting, data ingestion, compliance controls, etc.
Build what makes fraud response unique
Risk thresholds, decision logic, workflows, and policy rules vary by industry and business model. Building on top of a battle-tested foundation allows teams to tailor fraud responses without taking up the heavy burden of maintenance.
Avoid rebuilding non-differentiating layers
Recreating plumbing rarely creates advantage. Most organizations do not win on how they collect device signals. They win on how they apply them. The Build + Buy model preserves control where it matters, while removing drag where it does not.
Ways to Keep Pace With Evolving Fraud
Fraud is a moving target. Fraudsters change their tactics as soon as existing vulnerabilities are closed and new defenses are raised. Organizations can keep pace with evolving fraud schemes and ensure that their user data is protected with these tactics:

Skip the Burden, Focus on Outcomes
The build vs. buy debate no longer fits the reality of modern fraud prevention. Fraud systems must adapt fast, scale reliably, and meet growing compliance demands. That requires more than full ownership or outsourcing. Furthermore, the cost of fraud infrastructure is not limited to licenses or engineering hours. It includes opportunity cost, inherent risks, and fragmented efforts.
A better approach is to skip the burden and focus on fraud prevention outcomes. With Bureau businesses can reduce fraud losses, limit customer friction, and support investigators with clear, timely signals across the customer lifecycle.
Bureau’s Device ID delivers best-in-class fingerprinting with 99.7% device persistence in linking accounts and devices that helps reduce collusion-based abuse by over 95%. Powered by Bureau’s AI-driven Unified Risk Decisioning Platform, businesses can activate adaptive fraud responses from day one, while remaining compliant across regions. Bureau evaluates 200+ behavioral attributes and maps relationships across devices, accounts, and behaviors, to help modern businesses identify fraud rings and anomalies even when devices, credentials, or IPs appear clean.
Rethink device intelligence and fraud signals with Bureau to enable unified fraud decisioning across the customer lifecycle. Schedule a demo.
TABLE OF CONTENTS
See More
Recommended Blogs

How Middle East Banks Can Rethink Fraud Prevention
Rapid digital adoption is reshaping banking across the Middle East. Instant onboarding, digital wallets, and super apps are now the norm, expanding the attack surface in the process. To deliver strong protection without adding friction, banks in the region must counter AI-driven fraud with connected intelligence across identity, devices, and behavior.

Building Real-time Defenses in an Always-on Economy
In an always-on, connected economy, risks are created in real-time, rather than at discrete checkpoints. Defense strategies must, accordingly, level up to measure trust throughout the entire user experience, from first interaction to every single transaction. This always-on protection needs connected signals, adaptive decisioning, and protection that can keep pace with evolving digital behaviors and access methods.

iGaming KYC: Balancing Risk, Compliance, and Player Experience
KYC-driven identity verification is a core element for fraud prevention in iGaming. It helps these platforms establish trust at onboarding by creating a secure, fair, and sustainable ecosystem, preventing abuse, preserving integrity of the platform, and ensuring regulatory compliance.
TABLE OF CONTENTS
See Less


Solutions
Resources
© 2026 Bureau . All rights reserved.
Solutions
Industries
Resources
Company
Solutions
Industries
Resources
Company
© 2026 Bureau . All rights reserved.
Follow Us
Leave behind fragmented tools. Stop fraud rings, cut false declines, and deliver secure digital journeys at scale
Our Presence












Leave behind fragmented tools. Stop fraud rings, cut false declines, and deliver secure digital journeys at scale
Our Presence












© 2026 Bureau . All rights reserved.

